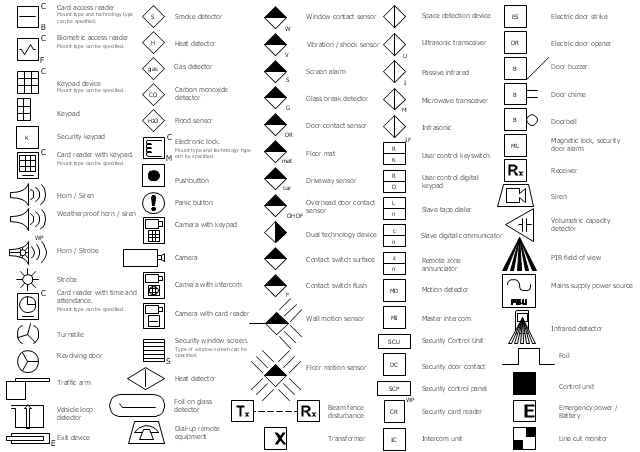
The vector stencils library Alarm and access control contains 80 symbols of digital proximity equipment, locking hardware, and access control equipment.
"An alarm device or system of alarm devices gives an audible, visual or other form of alarm signal about a problem or condition. Alarm devices are often outfitted with a siren." [Alarm device. Wikipedia]
"An access control point, which can be a door, turnstile, parking gate, elevator, or other physical barrier, where granting access can be electronically controlled. Typically, the access point is a door. An electronic access control door can contain several elements. At its most basic, there is a stand-alone electric lock. The lock is unlocked by an operator with a switch. To automate this, operator intervention is replaced by a reader. The reader could be a keypad where a code is entered, it could be a card reader, or it could be a biometric reader. Readers do not usually make an access decision, but send a card number to an access control panel that verifies the number against an access list. To monitor the door position a magnetic door switch can be used. In concept, the door switch is not unlike those on refrigerators or car doors. Generally only entry is controlled, and exit is uncontrolled. In cases where exit is also controlled, a second reader is used on the opposite side of the door. In cases where exit is not controlled, free exit, a device called a request-to-exit (REX) is used. Request-to-exit devices can be a push-button or a motion detector. When the button is pushed, or the motion detector detects motion at the door, the door alarm is temporarily ignored while the door is opened. Exiting a door without having to electrically unlock the door is called mechanical free egress. This is an important safety feature. In cases where the lock must be electrically unlocked on exit, the request-to-exit device also unlocks the door." [Access control. Wikipedia]
Use the design elements library Alarm and access control for drawing layout floor plans, blueprints, and wiring diagrams of intrusion systems, time and attendance systems, card and code access control security systems, internal and external security control systems using the ConceptDraw PRO diagramming and vector drawing software.
The shapes library Alarm and access control is included in the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
"An alarm device or system of alarm devices gives an audible, visual or other form of alarm signal about a problem or condition. Alarm devices are often outfitted with a siren." [Alarm device. Wikipedia]
"An access control point, which can be a door, turnstile, parking gate, elevator, or other physical barrier, where granting access can be electronically controlled. Typically, the access point is a door. An electronic access control door can contain several elements. At its most basic, there is a stand-alone electric lock. The lock is unlocked by an operator with a switch. To automate this, operator intervention is replaced by a reader. The reader could be a keypad where a code is entered, it could be a card reader, or it could be a biometric reader. Readers do not usually make an access decision, but send a card number to an access control panel that verifies the number against an access list. To monitor the door position a magnetic door switch can be used. In concept, the door switch is not unlike those on refrigerators or car doors. Generally only entry is controlled, and exit is uncontrolled. In cases where exit is also controlled, a second reader is used on the opposite side of the door. In cases where exit is not controlled, free exit, a device called a request-to-exit (REX) is used. Request-to-exit devices can be a push-button or a motion detector. When the button is pushed, or the motion detector detects motion at the door, the door alarm is temporarily ignored while the door is opened. Exiting a door without having to electrically unlock the door is called mechanical free egress. This is an important safety feature. In cases where the lock must be electrically unlocked on exit, the request-to-exit device also unlocks the door." [Access control. Wikipedia]
Use the design elements library Alarm and access control for drawing layout floor plans, blueprints, and wiring diagrams of intrusion systems, time and attendance systems, card and code access control security systems, internal and external security control systems using the ConceptDraw PRO diagramming and vector drawing software.
The shapes library Alarm and access control is included in the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
The vector stencils library "Access and security" contains 17 clipart images of access control and security system equipment which you can easy use in your diagrams and illustrations.
"Physical security describes security measures that are designed to deny unauthorized access to facilities, equipment and resources, and to protect personnel and property from damage or harm (such as espionage, theft, or terrorist attacks). Physical security involves the use of multiple layers of interdependent systems which include CCTV surveillance, security guards, protective barriers, locks, access control protocols, and many other techniques." [Physical security. Wikipedia]
The clip art example "Access and security - Vector stencils library" was created in the ConceptDraw PRO diagramming and vector drawing software using the Presentation Clipart solution from the Illustration area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ illustrations-presentation-clipart
"Physical security describes security measures that are designed to deny unauthorized access to facilities, equipment and resources, and to protect personnel and property from damage or harm (such as espionage, theft, or terrorist attacks). Physical security involves the use of multiple layers of interdependent systems which include CCTV surveillance, security guards, protective barriers, locks, access control protocols, and many other techniques." [Physical security. Wikipedia]
The clip art example "Access and security - Vector stencils library" was created in the ConceptDraw PRO diagramming and vector drawing software using the Presentation Clipart solution from the Illustration area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ illustrations-presentation-clipart
Cisco Products Additional. Cisco icons, shapes, stencils and symbols
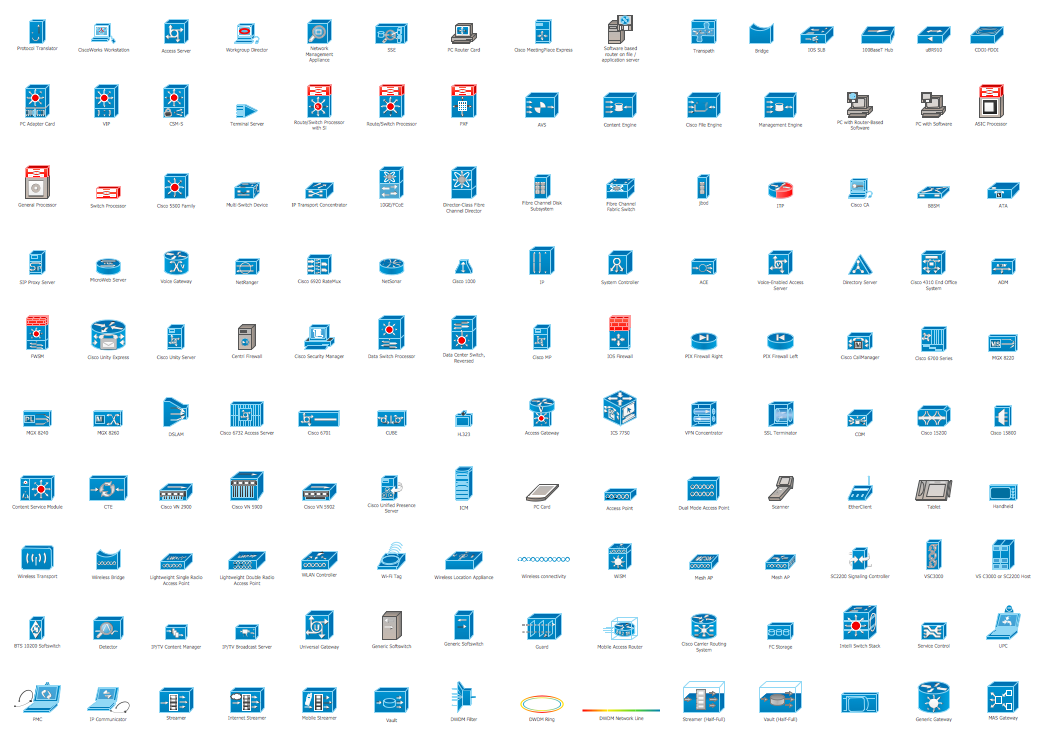
The ConceptDraw vector stencils library "Cisco Products Additional" contains equipment symbols for drawing the computer network diagrams.The vector stencils library "Cisco products additional" contains 141 symbols of computer network devices and equipment for drawing Cisco network diagrams.
The symbols example "Cisco products additional - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
The symbols example "Cisco products additional - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
The vector stencils library "Cisco products additional" contains 141 symbols of computer network devices and equipment for drawing Cisco network diagrams.
The symbols example "Cisco products additional - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
The symbols example "Cisco products additional - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
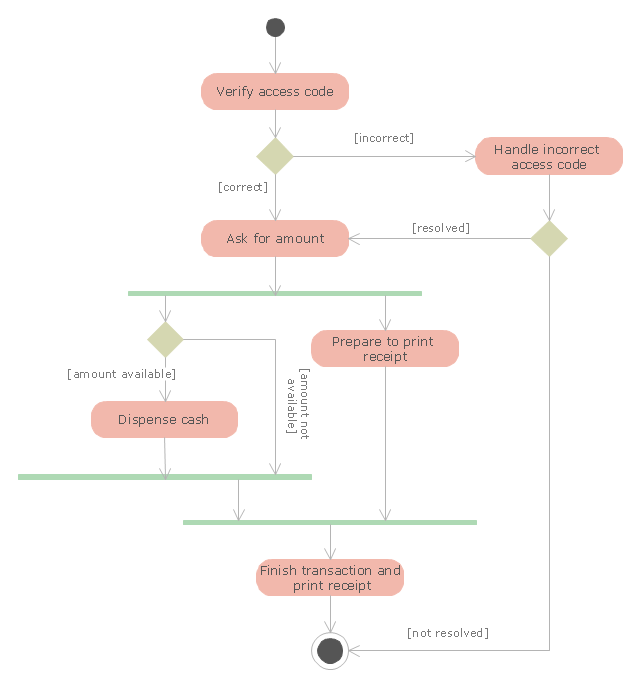
"An automated teller machine or automatic teller machine" (ATM) (American, Australian, Singaporean, Indian, and Hiberno-English), also known as an automated banking machine (ABM) (Canadian English), cash machine, cashpoint, cashline or hole in the wall (British, South African, and Sri Lankan English), is an electronic telecommunications device that enables the clients of a financial institution to perform financial transactions without the need for a cashier, human clerk or bank teller.
On most modern ATMs, the customer is identified by inserting a plastic ATM card with a magnetic stripe or a plastic smart card with a chip that contains a unique card number and some security information such as an expiration date or CVVC (CVV). Authentication is provided by the customer entering a personal identification number (PIN). The newest ATM at Royal Bank of Scotland allows customers to withdraw cash up to £100 without a card by inputting a six-digit code requested through their smartphones.
Using an ATM, customers can access their bank accounts in order to make cash withdrawals, get debit card cash advances, and check their account balances as well as purchase pre-paid mobile phone credit. If the currency being withdrawn from the ATM is different from that which the bank account is denominated in (e.g.: Withdrawing Japanese yen from a bank account containing US dollars), the money will be converted at an official wholesale exchange rate. Thus, ATMs often provide one of the best possible official exchange rates for foreign travellers, and are also widely used for this purpose." [Automated teller machine. Wikipedia]
The UML activity diagram example "Cash withdrawal from ATM" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Rapid UML solution from the Software Development area of ConceptDraw Solution Park.
On most modern ATMs, the customer is identified by inserting a plastic ATM card with a magnetic stripe or a plastic smart card with a chip that contains a unique card number and some security information such as an expiration date or CVVC (CVV). Authentication is provided by the customer entering a personal identification number (PIN). The newest ATM at Royal Bank of Scotland allows customers to withdraw cash up to £100 without a card by inputting a six-digit code requested through their smartphones.
Using an ATM, customers can access their bank accounts in order to make cash withdrawals, get debit card cash advances, and check their account balances as well as purchase pre-paid mobile phone credit. If the currency being withdrawn from the ATM is different from that which the bank account is denominated in (e.g.: Withdrawing Japanese yen from a bank account containing US dollars), the money will be converted at an official wholesale exchange rate. Thus, ATMs often provide one of the best possible official exchange rates for foreign travellers, and are also widely used for this purpose." [Automated teller machine. Wikipedia]
The UML activity diagram example "Cash withdrawal from ATM" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Rapid UML solution from the Software Development area of ConceptDraw Solution Park.
The vector stencils library "Electrical and telecom" contains 83 symbols of electrical and telecommunication equipment.
Use these shapes for drawing electrical and telecom system design floor plans, cabling layout schemes, and wiring diagrams in the ConceptDraw PRO diagramming and vector drawing software extended with the Electric and Telecom Plans solution from the Building Plans area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ building-electric-telecom-plans
Use these shapes for drawing electrical and telecom system design floor plans, cabling layout schemes, and wiring diagrams in the ConceptDraw PRO diagramming and vector drawing software extended with the Electric and Telecom Plans solution from the Building Plans area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ building-electric-telecom-plans
 Security and Access Plans
Security and Access Plans
This solution extends ConceptDraw PRO software with samples, templates and libraries of design elements for drawing the Security and Access Plan.
"IVR systems are typically intended to service high call volumes, reduce cost and improve the customer experience. Examples of typical IVR applications are telephone banking, televoting, and credit card services. ...
Voice-Activated Dialing
... (VAD) IVR systems are used to automate routine enquiries to switchboard or PABX (Private Automatic Branch eXchange) operators, and are used in many hospitals and large businesses to reduce the caller waiting time. ...
Entertainment and information.
Some of the largest installed IVR platforms are used for televoting on television game shows, ... which can generate enormous call spikes. Often, the network provider will have to deploy call gapping in the PSTN to prevent network overload. ...
Anonymous access.
IVR systems allow callers to obtain data relatively anonymously. Hospitals and clinics have used IVR systems to allow callers to receive anonymous access to test results. ...
Clinical trials.
IVR systems are used by pharmaceutical companies and contract research organizations to conduct clinical trials and manage the large volumes of data generated. ... Applications include patient randomization and drug supply management. ...
Outbound calling.
IVR systems can be used for outbound calls, as IVR systems are more intelligent than many predictive dialer systems, and can use Call Progress Detection to recognize different line conditions...
Other common IVR services include:
Mobile - Pay-As-You-Go account funding; registration; mobile purchases, such as ring tones and logos;
Banking - balance, payments, transfers, transaction history;
Retail & Entertainment - orders, bookings, credit & debit card payments;
Utilities - meter readings; account look-up, history and balance, payment, consumption history;
Travel — ticket booking, flight information, check-in;
Weather forecasts, water, road and ice conditions" [Interactive voice response. Wikipedia]
The IVR services diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Interactive Voice Response Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-IVR
Voice-Activated Dialing
... (VAD) IVR systems are used to automate routine enquiries to switchboard or PABX (Private Automatic Branch eXchange) operators, and are used in many hospitals and large businesses to reduce the caller waiting time. ...
Entertainment and information.
Some of the largest installed IVR platforms are used for televoting on television game shows, ... which can generate enormous call spikes. Often, the network provider will have to deploy call gapping in the PSTN to prevent network overload. ...
Anonymous access.
IVR systems allow callers to obtain data relatively anonymously. Hospitals and clinics have used IVR systems to allow callers to receive anonymous access to test results. ...
Clinical trials.
IVR systems are used by pharmaceutical companies and contract research organizations to conduct clinical trials and manage the large volumes of data generated. ... Applications include patient randomization and drug supply management. ...
Outbound calling.
IVR systems can be used for outbound calls, as IVR systems are more intelligent than many predictive dialer systems, and can use Call Progress Detection to recognize different line conditions...
Other common IVR services include:
Mobile - Pay-As-You-Go account funding; registration; mobile purchases, such as ring tones and logos;
Banking - balance, payments, transfers, transaction history;
Retail & Entertainment - orders, bookings, credit & debit card payments;
Utilities - meter readings; account look-up, history and balance, payment, consumption history;
Travel — ticket booking, flight information, check-in;
Weather forecasts, water, road and ice conditions" [Interactive voice response. Wikipedia]
The IVR services diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Interactive Voice Response Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-IVR
 Holiday
Holiday
The Holiday Solution from Illustration area of ConceptDraw Solution Park contains holiday illustration examples, templates and vector clipart library.
 Rapid UML
Rapid UML
Rapid UML solution extends ConceptDraw PRO software with templates, samples and libraries of vector stencils for quick drawing the UML diagrams using Rapid Draw technology.
The vector stencils library "Access and security" contains 17 clipart images of access control and security system equipment which you can easy use in your diagrams and illustrations.
"Physical security describes security measures that are designed to deny unauthorized access to facilities, equipment and resources, and to protect personnel and property from damage or harm (such as espionage, theft, or terrorist attacks). Physical security involves the use of multiple layers of interdependent systems which include CCTV surveillance, security guards, protective barriers, locks, access control protocols, and many other techniques." [Physical security. Wikipedia]
The clip art example "Access and security - Vector stencils library" was created in the ConceptDraw PRO diagramming and vector drawing software using the Presentation Clipart solution from the Illustration area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ illustrations-presentation-clipart
"Physical security describes security measures that are designed to deny unauthorized access to facilities, equipment and resources, and to protect personnel and property from damage or harm (such as espionage, theft, or terrorist attacks). Physical security involves the use of multiple layers of interdependent systems which include CCTV surveillance, security guards, protective barriers, locks, access control protocols, and many other techniques." [Physical security. Wikipedia]
The clip art example "Access and security - Vector stencils library" was created in the ConceptDraw PRO diagramming and vector drawing software using the Presentation Clipart solution from the Illustration area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ illustrations-presentation-clipart
- Credit Card Processing System UML Diagram | Credit Card Order ...
- Design elements - Alarm and access control | Interactive voice ...
- Design elements - Alarm and access control | How To Create Home ...
- Design elements - Alarm and access control | Design elements - Site ...
- Design elements - Alarm and access control | Design elements - Site ...
- Interior Design Plumbing - Design Elements | How To Create ...
- UML Deployment Diagram. Design Elements ... - Conceptdraw.com
- Accounting flowcharts - Vector stencils library ... - Conceptdraw.com
- Security and Access Plans | Sales Dashboard - Access Anywhere ...
- Design elements - Doors and windows | Design elements - Alarm ...
- UML activity diagram - Cash withdrawal from ATM | IVR services ...
- Wireless access point - Network diagram | Roaming wireless local ...
- UML sequence diagram - GET request | Trouble ticket system ...
- How To Create Restaurant Floor Plans in Minutes | Blueprint ...
- Design elements - Fire and emergency planning | IDEF9 Standard ...
- Design elements - Video surveillance | Design elements - Alarm and ...
- How To Create Restaurant Floor Plans in Minutes | How To Draw ...
- Security and Access Plans | Design elements - Alarm and access ...
- Security and Access Plans | Design elements - Alarm and access ...
- Design elements - Fire safety equipment | Safety and Security | Fire ...



















-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)






-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)

-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)

















-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)


-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)



-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)















-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)


-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)















-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)



-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)


-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)




-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-products-additional---vector-stencils-library.png--diagram-flowchart-example.png)