Cyber Security Degrees
For protection various cyber environments are developed and applied large variety of cyber security standards, techniques, security concepts and approaches with different cyber security degrees. The ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park offers the number of useful tools which will help network security engineers, cyber security specialists, network and computer analysts easily and visually depict the knowledge and skills for research and prevention of intrusions, about protection critical information and analysis of cyber incidents, and for how to assess threats and vulnerabilities.IT Security Solutions
Dynamic of development computer and network technologies increases the need in modern cyber security strategies and IT security solutions to support security of your data, to ensure data privacy, and to protect your operations from the cyber threats. Thanks to the Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park, the ConceptDraw PRO diagramming and vector drawing software is one of the unique IT security solutions for professional designing Network Security Diagrams.Network Security Devices
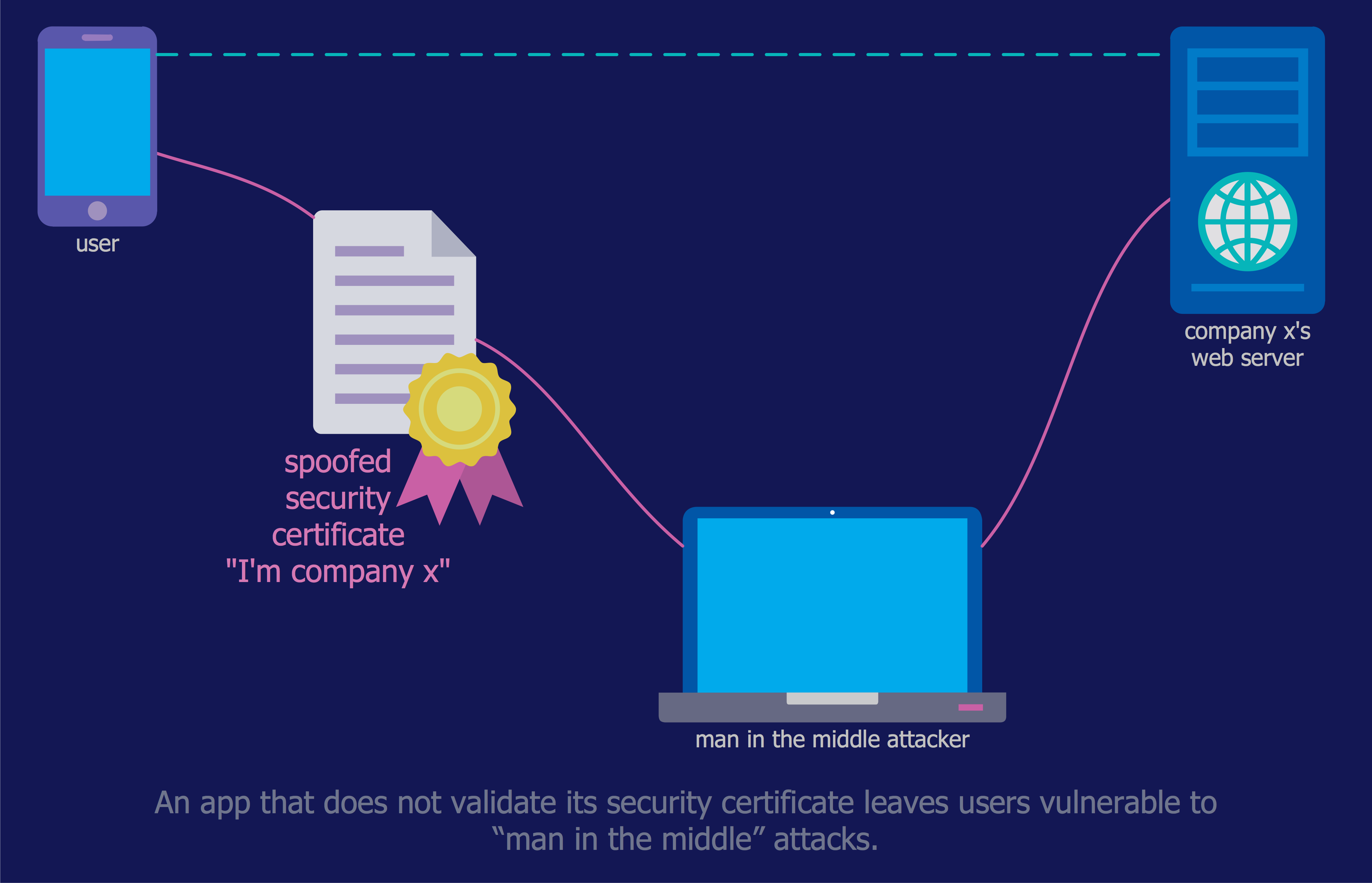
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.This example was designed on the base of the diagram from the "BYOD Guidance: BlackBerry Secure Work Space" on the website of the UK Communications Electronics Security Group (CESG).
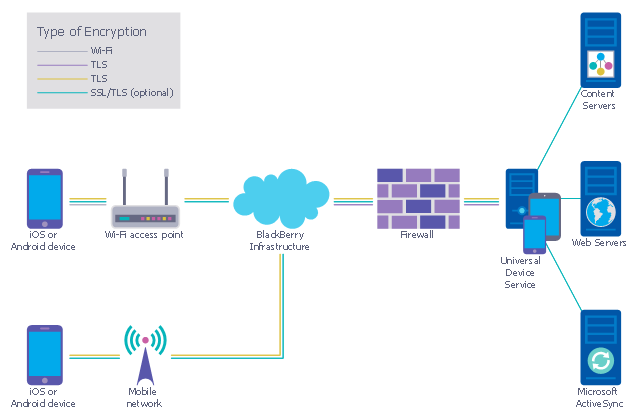
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
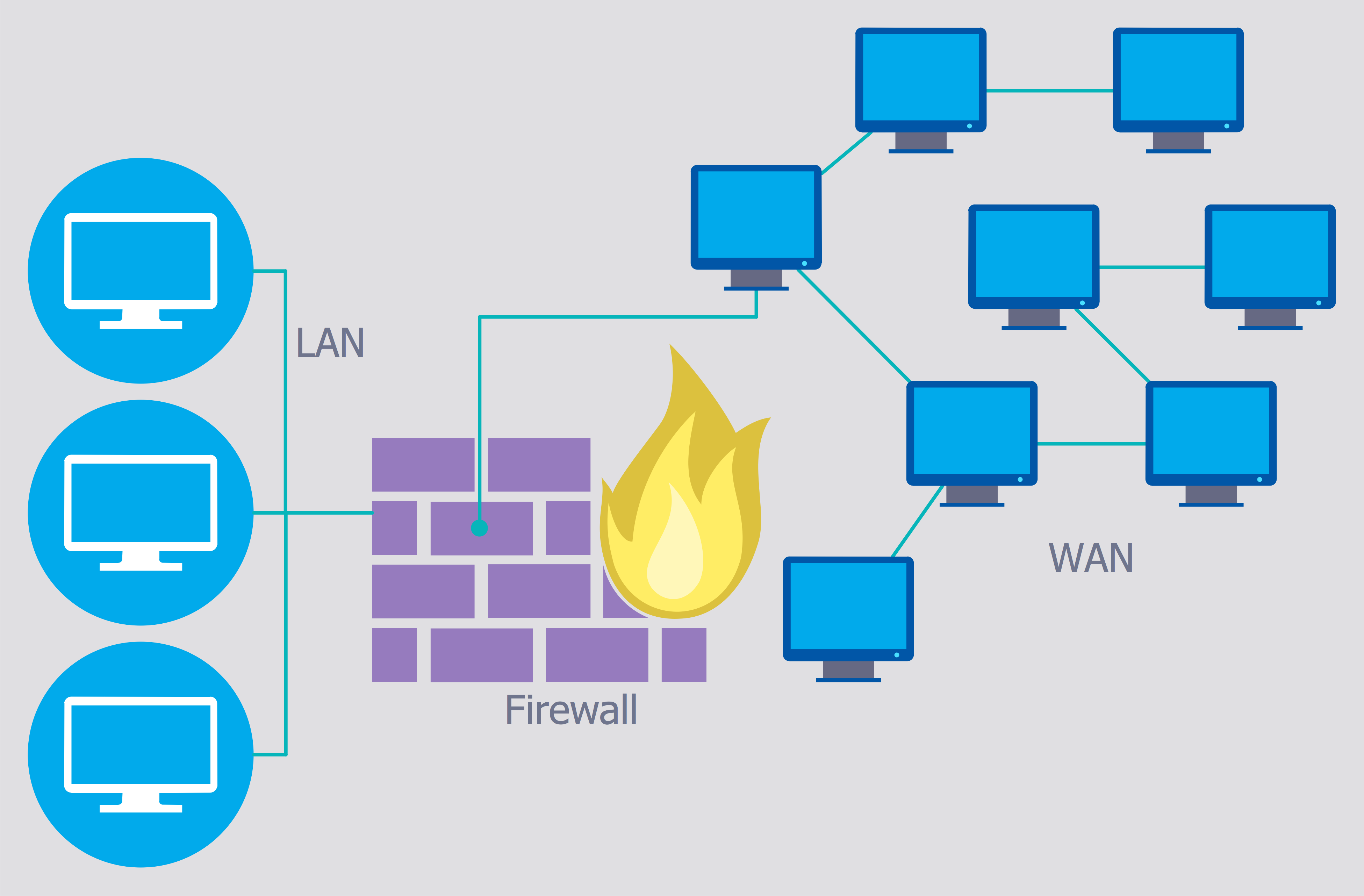
Secure Wireless Network
Use the ConceptDraw PRO diagramming and vector drawing software enhanced with powerful tools of Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park to effectively visualize the importance of network security and wireless network security, and ways to ensure them, to easily design Network Security Diagrams and Maps, Network Security Model, Secure Wireless Network and Network Security Architecture diagrams.
 ConceptDraw Solution Park
ConceptDraw Solution Park
ConceptDraw Solution Park collects graphic extensions, examples and learning materials
 Seven Management and Planning Tools
Seven Management and Planning Tools
Seven Management and Planning Tools solution extends ConceptDraw PRO and ConceptDraw MINDMAP with features, templates, samples and libraries of vector stencils for drawing management mind maps and diagrams.
 Management Area
Management Area
The solutions from Management area of ConceptDraw Solution Park collect templates, samples and libraries of vector stencils for drawing the management diagrams and mind maps.
How to Design Landscape
How to design landscape? You can draw it by hand on a sheet of paper, but for this you need to know the bases of the perspective, you need to have good artistic abilities and to know how to depict the natural elements. But it is much easier and convenient to use the modern ConceptDraw PRO diagramming and vector drawing software extended with Landscape & Garden Solution from the Building Plans Area.
 Concept Maps
Concept Maps
The technique of concept mapping was developed as a constructive way of representing knowledge in science and increasing the meaningfulness of learning. Now, the creation of a concept map is extremely helpful when used in education as learning and teaching techniques that assist memorization. Concept maps are also used for idea generation in brainstorming sessions, and for detailing the structure of complex ideas.
HelpDesk
Agile Mind Maps: Exploring the User Wishes
Agile method advocate use cases and user stories, but there are no standard processes or guides available to help gather user requirements. That is why documenting user requirements can be challenging. Without strong communication experience the scrum process can collapse, leading towards unfruitful requirements and imperfect software. This article offers a path to overcome these hurdles through the simplicity and clearness of mind mapping. ConceptDraw Scrum Worflow solution lets explore the user requirements for your Agile development project before they are formalized. You can easily create professional Mind Maps that will effectively collect and structure the information on what a user actually wants, or the “User Wish.”Business - Design Elements
Choose which of business design elements you love best.Design your own style with Business and Finance Solutions from ConceptDraw PRO.
We created a full set of elements, business samples, templates and libraries with vector clip art for drawing the Business Illustrations.
Mark your report or presentation, pay an attention of audience on your drawings with vector business design elements.
- Computer Security Risks
- Network Security Risk
- IT Security Solutions | Cyber Security Degrees | Network Security ...
- Cyber Security Risk
- Network Security Devices | Cyber Security Degrees | ConceptDraw ...
- Cyber Security Degrees | Network Security Devices | IT Security ...
- Network Security Diagrams | Cyber Security Degrees | Network ...
- IT Security Solutions | Network Security Devices | Cyber Security ...
- Computer Security Solutions
- Network Security Diagrams | ConceptDraw Solution Park | Computer ...
- Cyber Security Degrees | Network Security Diagrams | Computer ...
- Cyber Security Degrees | 10 Steps to Cyber Security | Network ...
- Network Security Diagrams | Network Security | How to Create a ...
- Computer Security Problems
- IT Security Solutions | Network Security Diagrams | Computer and ...
- Computer Security Report
- Cyber Security Degrees | How to Create a Network Security ...
- Network Security | Cyber Security Degrees | | Computer Security Tools
- Cyber Security Degrees | | Network Security Devices | Computer ...