The vector stencils library "Microsoft Exchange" contains 17 symbols of Microsoft Exchange elements for drawing the logical structure diagrams of Active Directory trees.
"Microsoft Exchange Server is calendaring software, a mail server and contact manager developed by Microsoft. It is a server program that runs on Windows Server and is part of the Microsoft Servers line of products." [Microsoft Exchange Server. Wikipedia]
The shapes example "Design elements - Microsoft Exchange" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"Microsoft Exchange Server is calendaring software, a mail server and contact manager developed by Microsoft. It is a server program that runs on Windows Server and is part of the Microsoft Servers line of products." [Microsoft Exchange Server. Wikipedia]
The shapes example "Design elements - Microsoft Exchange" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
 Active Directory Diagrams
Active Directory Diagrams
Active Directory Diagrams solution extends ConceptDraw PRO software with samples, templates and libraries of vector stencils for drawing the AD diagrams to visualize the detail structures of the Microsoft Windows networks.
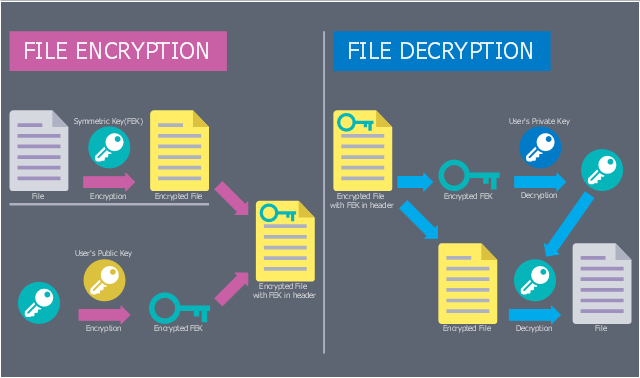
This computer security diagram example was designed on the base of Wikimedia Commons file: EFSOperation.svg.
"Flowchart for the operation of Encrypting File System (EFS)" [commons.wikimedia.org/ wiki/ File:EFSOperation.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"The Encrypting File System (EFS) on Microsoft Windows is a feature introduced in version 3.0 of NTFS that provides filesystem-level encryption. The technology enables files to be transparently encrypted to protect confidential data from attackers with physical access to the computer.
EFS is available in all versions of Windows developed for business environments from Windows 2000 onwards. By default, no files are encrypted, but encryption can be enabled by users on a per-file, per-directory, or per-drive basis. Some EFS settings can also be mandated via Group Policy in Windows domain environments." [Encrypting File System. Wikipedia]
The cybersecurity diagram example "EFS Operation" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Flowchart for the operation of Encrypting File System (EFS)" [commons.wikimedia.org/ wiki/ File:EFSOperation.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"The Encrypting File System (EFS) on Microsoft Windows is a feature introduced in version 3.0 of NTFS that provides filesystem-level encryption. The technology enables files to be transparently encrypted to protect confidential data from attackers with physical access to the computer.
EFS is available in all versions of Windows developed for business environments from Windows 2000 onwards. By default, no files are encrypted, but encryption can be enabled by users on a per-file, per-directory, or per-drive basis. Some EFS settings can also be mandated via Group Policy in Windows domain environments." [Encrypting File System. Wikipedia]
The cybersecurity diagram example "EFS Operation" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
 Block Diagrams
Block Diagrams
Block diagrams solution extends ConceptDraw PRO software with templates, samples and libraries of vector stencils for drawing the block diagrams.
"SWOT analysis is a classic strategic planning tool. Using a framework of internal strengths and weaknesses and external opportunities and threats, it provides a simple way to assess how a strategy can best be implemented. The tool helps planners be realistic about what they can achieve, and where they should focus. ...
The SWOT framework - a two-by-two matrix - is best completed in a group with key members of the team or organisation present. First it is important to be clear what the policy change objective is, and what team or organisation the analysis is being carried out on. Once these are clarified and agreed, begin with a brainstorm of ideas, and then hone them down and clarify them afterwards in discussion.
An assessment of internal capacity helps identify where the project or organisation is now: the existing resources that can be used immediately and current problems that won't go away. It can help identify where new resources, skills or allies will be needed. When thinking of strengths it is useful to think of real examples of success to ground and clarify the conversation. ...
An assessment of the external environment tends to focus on what is going on outside the organisation, or areas which are not yet affecting the strategy but could do - either positively or negatively." [odi.org.uk/ publications/ 5876-swot-analysis-context-mapping]
The vector stencils library "SWOT" contains 16 SWOT and TOWS matrix diagram templates for the ConceptDraw PRO diagramming and vector drawing software.
The example "Design elements - SWOT and TOWS analysis matrices" is included in the SWOT Analysis solution from the Management area of ConceptDraw Solution Park.
The SWOT framework - a two-by-two matrix - is best completed in a group with key members of the team or organisation present. First it is important to be clear what the policy change objective is, and what team or organisation the analysis is being carried out on. Once these are clarified and agreed, begin with a brainstorm of ideas, and then hone them down and clarify them afterwards in discussion.
An assessment of internal capacity helps identify where the project or organisation is now: the existing resources that can be used immediately and current problems that won't go away. It can help identify where new resources, skills or allies will be needed. When thinking of strengths it is useful to think of real examples of success to ground and clarify the conversation. ...
An assessment of the external environment tends to focus on what is going on outside the organisation, or areas which are not yet affecting the strategy but could do - either positively or negatively." [odi.org.uk/ publications/ 5876-swot-analysis-context-mapping]
The vector stencils library "SWOT" contains 16 SWOT and TOWS matrix diagram templates for the ConceptDraw PRO diagramming and vector drawing software.
The example "Design elements - SWOT and TOWS analysis matrices" is included in the SWOT Analysis solution from the Management area of ConceptDraw Solution Park.
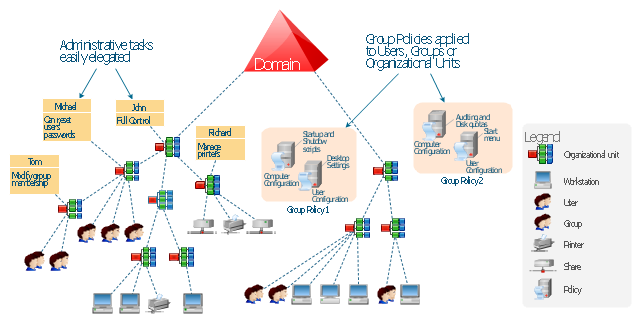
This example was drawn on the base of the Figure 2 illustrating the "Active Directory FAQ" from the website "Information Management Systems & Services" (IMSS) of the California Institute of Technology (Caltech) campus. [imss.caltech.edu/ node/ 412]
"By using the Active Directory® Domain Services (AD DS) server role, you can create a scalable, secure, and manageable infrastructure for user and resource management, and you can provide support for directory-enabled applications, such as Microsoft® Exchange Server. ...
AD DS provides a distributed database that stores and manages information about network resources and application-specific data from directory-enabled applications. Administrators can use AD DS to organize elements of a network, such as users, computers, and other devices, into a hierarchical containment structure. The hierarchical containment structure includes the Active Directory forest, domains in the forest, and organizational units (OUs) in each domain. A server that is running AD DS is called a domain controller." [technet.microsoft.com/ en-us/ library/ 9a5cba91-7153-4265-adda-c70df2321982]
The Active Directory Domain Services diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"By using the Active Directory® Domain Services (AD DS) server role, you can create a scalable, secure, and manageable infrastructure for user and resource management, and you can provide support for directory-enabled applications, such as Microsoft® Exchange Server. ...
AD DS provides a distributed database that stores and manages information about network resources and application-specific data from directory-enabled applications. Administrators can use AD DS to organize elements of a network, such as users, computers, and other devices, into a hierarchical containment structure. The hierarchical containment structure includes the Active Directory forest, domains in the forest, and organizational units (OUs) in each domain. A server that is running AD DS is called a domain controller." [technet.microsoft.com/ en-us/ library/ 9a5cba91-7153-4265-adda-c70df2321982]
The Active Directory Domain Services diagram example was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
The vector stencils library "Active Directory" contains 20 symbols of Active Directory objects for drawing AD network diagrams. It helps network and system administrators to visualize Microsoft Windows Active Directory structures for network design, installation and maintainance.
"Objects.
An Active Directory structure is an arrangement of information about objects. The objects fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Security principals are assigned unique security identifiers (SIDs).
Each object represents a single entity - whether a user, a computer, a printer, or a group - and its attributes. Certain objects can contain other objects. An object is uniquely identified by its name and has a set of attributes - the characteristics and information that the object represents - defined by a schema, which also determines the kinds of objects that can be stored in Active Directory.
The schema object lets administrators extend or modify the schema when necessary. However, because each schema object is integral to the definition of Active Directory objects, deactivating or changing these objects can fundamentally change or disrupt a deployment. Schema changes automatically propagate throughout the system. Once created, an object can only be deactivated - not deleted. Changing the schema usually requires planning. Sites are implemented as a set of well-connected subnets." [Active Directory. Wikipedia]
The shapes example "Design elements - Active Directory" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"Objects.
An Active Directory structure is an arrangement of information about objects. The objects fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Security principals are assigned unique security identifiers (SIDs).
Each object represents a single entity - whether a user, a computer, a printer, or a group - and its attributes. Certain objects can contain other objects. An object is uniquely identified by its name and has a set of attributes - the characteristics and information that the object represents - defined by a schema, which also determines the kinds of objects that can be stored in Active Directory.
The schema object lets administrators extend or modify the schema when necessary. However, because each schema object is integral to the definition of Active Directory objects, deactivating or changing these objects can fundamentally change or disrupt a deployment. Schema changes automatically propagate throughout the system. Once created, an object can only be deactivated - not deleted. Changing the schema usually requires planning. Sites are implemented as a set of well-connected subnets." [Active Directory. Wikipedia]
The shapes example "Design elements - Active Directory" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
- Group Policy Diagram Windows
- Organizational Units | Design elements - Active Directory | Windows ...
- Active Directory Group Policy Drawing
- Computer Security Policy
- Bubble diagrams in Landscape Design with ConceptDraw PRO ...
- Active Directory Diagram | Active Directory Domain Services | Active ...
- Process Flowchart | Block Diagram Of Email Inner Working
- Examples Of Diagram Of Business Policy
- Active Directory Domain Services
- Hr Policy Management Flow Chart Dayagram
- AWS simple icons v2.0 - Vector stencils library | Design elements ...
- Block Diagram Of Security Policy And Other Diagram
- Warehouse Policy Sample
- Diagrams Of Business Policy
- Business Policy Diagrams
- Security Policy Diagram
- Active Directory Group User Directories
- Business Policy Diagram
- Security Policy And Block Diagram
- Windows 8 User Interface | How to Edit Grouped Shapes in ...