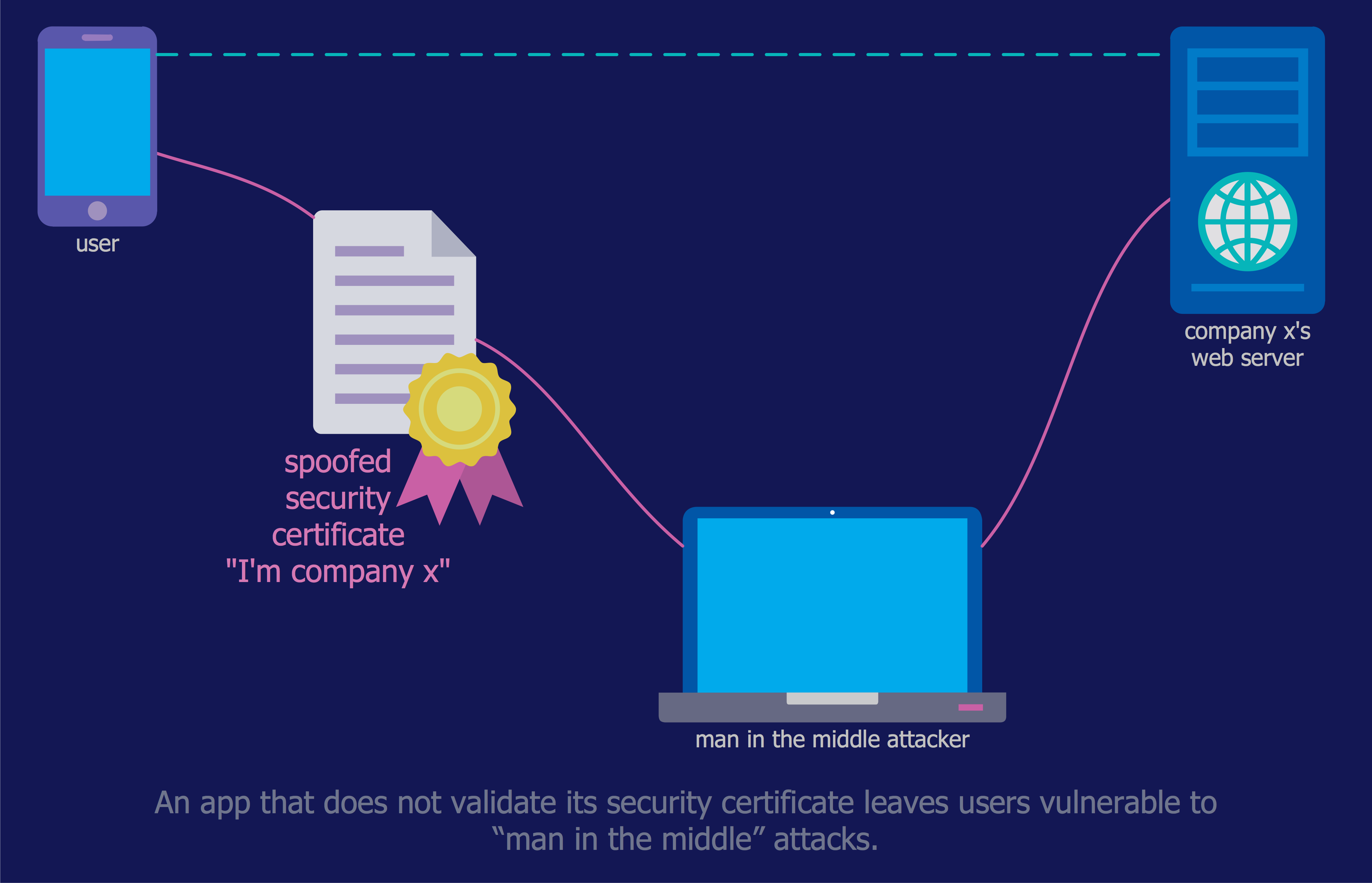
IT Security Solutions
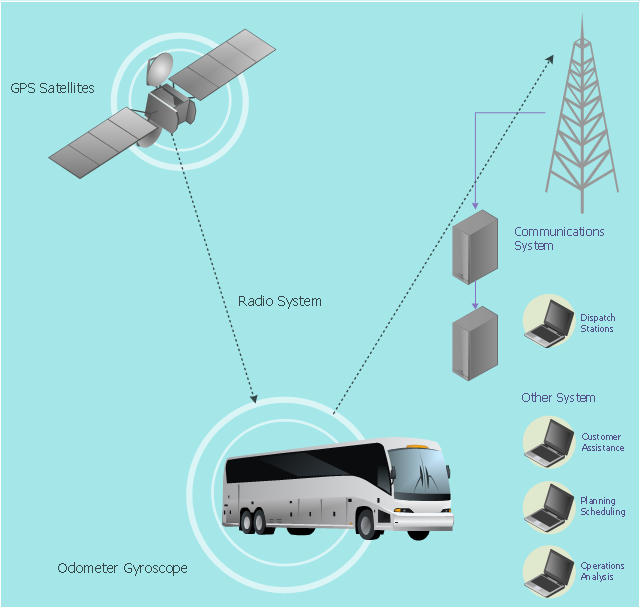
Dynamic of development computer and network technologies increases the need in modern cyber security strategies and IT security solutions to support security of your data, to ensure data privacy, and to protect your operations from the cyber threats. Thanks to the Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park, the ConceptDraw PRO diagramming and vector drawing software is one of the unique IT security solutions for professional designing Network Security Diagrams.This vehicular network diagram example was drawn on the base of picture illustrating the article "Automatic Vehicle Location: Rural Transit" from the website of the Research and Innovative Technology Administration (RITA), U.S. Department of Transportation (US DOT).
"Automatic Vehicle Location (AVL) systems calculate the real-time location of any vehicle equipped with a Global Positioning Satellite (GPS) receiver. Data are then transmitted to the transit center with use of radio or cellular communications and can be used immediately for daily operations as well as archived for further analysis.
As a stand-alone technology, an AVL system can be used to monitor on-time performance. When combined with other technologies, AVL can deliver many benefits in the areas of fleet management, service planning, safety and security, traveler information, fare payment, vehicle component monitoring, and data collection. Since the greatest benefits from AVL are achieved by combining it with other Intelligent Transportation System (ITS) technologies, AVL is most appropriate for large rural agencies with more than 30 vehicles that plan to implement a comprehensive ITS."
[pcb.its.dot.gov/ factsheets/ avl/ avlRural_ overview.asp]
The vehicular network diagram example "Automatic vehicle location" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Vehicular Networking solution from the Computer and Networks area of ConceptDraw Solution Park.
"Automatic Vehicle Location (AVL) systems calculate the real-time location of any vehicle equipped with a Global Positioning Satellite (GPS) receiver. Data are then transmitted to the transit center with use of radio or cellular communications and can be used immediately for daily operations as well as archived for further analysis.
As a stand-alone technology, an AVL system can be used to monitor on-time performance. When combined with other technologies, AVL can deliver many benefits in the areas of fleet management, service planning, safety and security, traveler information, fare payment, vehicle component monitoring, and data collection. Since the greatest benefits from AVL are achieved by combining it with other Intelligent Transportation System (ITS) technologies, AVL is most appropriate for large rural agencies with more than 30 vehicles that plan to implement a comprehensive ITS."
[pcb.its.dot.gov/ factsheets/ avl/ avlRural_ overview.asp]
The vehicular network diagram example "Automatic vehicle location" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Vehicular Networking solution from the Computer and Networks area of ConceptDraw Solution Park.
Used Solutions
"Surveillance is the monitoring of the behavior, activities, or other changing information, usually of people for the purpose of influencing, managing, directing, or protecting them. This can include observation from a distance by means of electronic equipment (such as CCTV cameras), or interception of electronically transmitted information (such as Internet traffic or phone calls); and it can include simple, relatively no- or low-technology methods such as human intelligence agents and postal interception. ...
Surveillance is very useful to governments and law enforcement to maintain social control, recognize and monitor threats, and prevent/ investigate criminal activity. With the advent of programs such as the Total Information Awareness program and ADVISE, technologies such as high speed surveillance computers and biometrics software, and laws such as the Communications Assistance For Law Enforcement Act, governments now possess an unprecedented ability to monitor the activities of their subjects." [Surveillance. Wikipedia]
[itl.nist.gov/ iad/ 894.01/ tests/ avss/ 2009/ ]
The example "Camera layout schematic" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
Surveillance is very useful to governments and law enforcement to maintain social control, recognize and monitor threats, and prevent/ investigate criminal activity. With the advent of programs such as the Total Information Awareness program and ADVISE, technologies such as high speed surveillance computers and biometrics software, and laws such as the Communications Assistance For Law Enforcement Act, governments now possess an unprecedented ability to monitor the activities of their subjects." [Surveillance. Wikipedia]
[itl.nist.gov/ iad/ 894.01/ tests/ avss/ 2009/ ]
The example "Camera layout schematic" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Security and Access Plans solution from the Building Plans area of ConceptDraw Solution Park.
"Microsoft SharePoint is a Web application platform developed by Microsoft. First launched in 2001, SharePoint has historically been associated with intranet, content management and document management, but recent versions have significantly broader capabilities.
SharePoint comprises a multipurpose set of Web technologies backed by a common technical infrastructure. By default, SharePoint has a Microsoft Office-like interface, and it is closely integrated with the Office suite. The web tools are designed to be usable by non-technical users. SharePoint can be used to provide intranet portals, document & file management, collaboration, social networks, extranets, websites, enterprise search, and business intelligence. It also has system integration, process integration, and workflow automation capabilities.
Enterprise application software (e.g. ERP or CRM packages) often provide some SharePoint integration capability, and SharePoint also incorporates a complete development stack based on web technologies and standards-based APIs. As an application platform, SharePoint provides central management, governance, and security controls for implementation of these requirements. The SharePoint platform integrates directly into IIS - enabling bulk management, scaling, and provisioning of servers, as is often required by large organizations or cloud hosting providers." [Microsoft SharePoint. Wikipedia]
The AWS architecture diagram example "SharePoint server reference architecture for public-facing website scenario" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
SharePoint comprises a multipurpose set of Web technologies backed by a common technical infrastructure. By default, SharePoint has a Microsoft Office-like interface, and it is closely integrated with the Office suite. The web tools are designed to be usable by non-technical users. SharePoint can be used to provide intranet portals, document & file management, collaboration, social networks, extranets, websites, enterprise search, and business intelligence. It also has system integration, process integration, and workflow automation capabilities.
Enterprise application software (e.g. ERP or CRM packages) often provide some SharePoint integration capability, and SharePoint also incorporates a complete development stack based on web technologies and standards-based APIs. As an application platform, SharePoint provides central management, governance, and security controls for implementation of these requirements. The SharePoint platform integrates directly into IIS - enabling bulk management, scaling, and provisioning of servers, as is often required by large organizations or cloud hosting providers." [Microsoft SharePoint. Wikipedia]
The AWS architecture diagram example "SharePoint server reference architecture for public-facing website scenario" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
 Marketing Diagrams
Marketing Diagrams
This solution extends ConceptDraw PRO with samples, templates and library of design elements for drawing the marketing diagrams.
 Wireless Networks
Wireless Networks
Wireless Networks solution extends ConceptDraw PRO software with templates, samples and vector stencils library for drawing the wireless computer communication network diagrams.
 Network Layout Floor Plans
Network Layout Floor Plans
Network Layout Floor Plan solution extends ConceptDraw PR software with samples, templates and libraries of vector stencils for drawing the computer network layout floor plans.
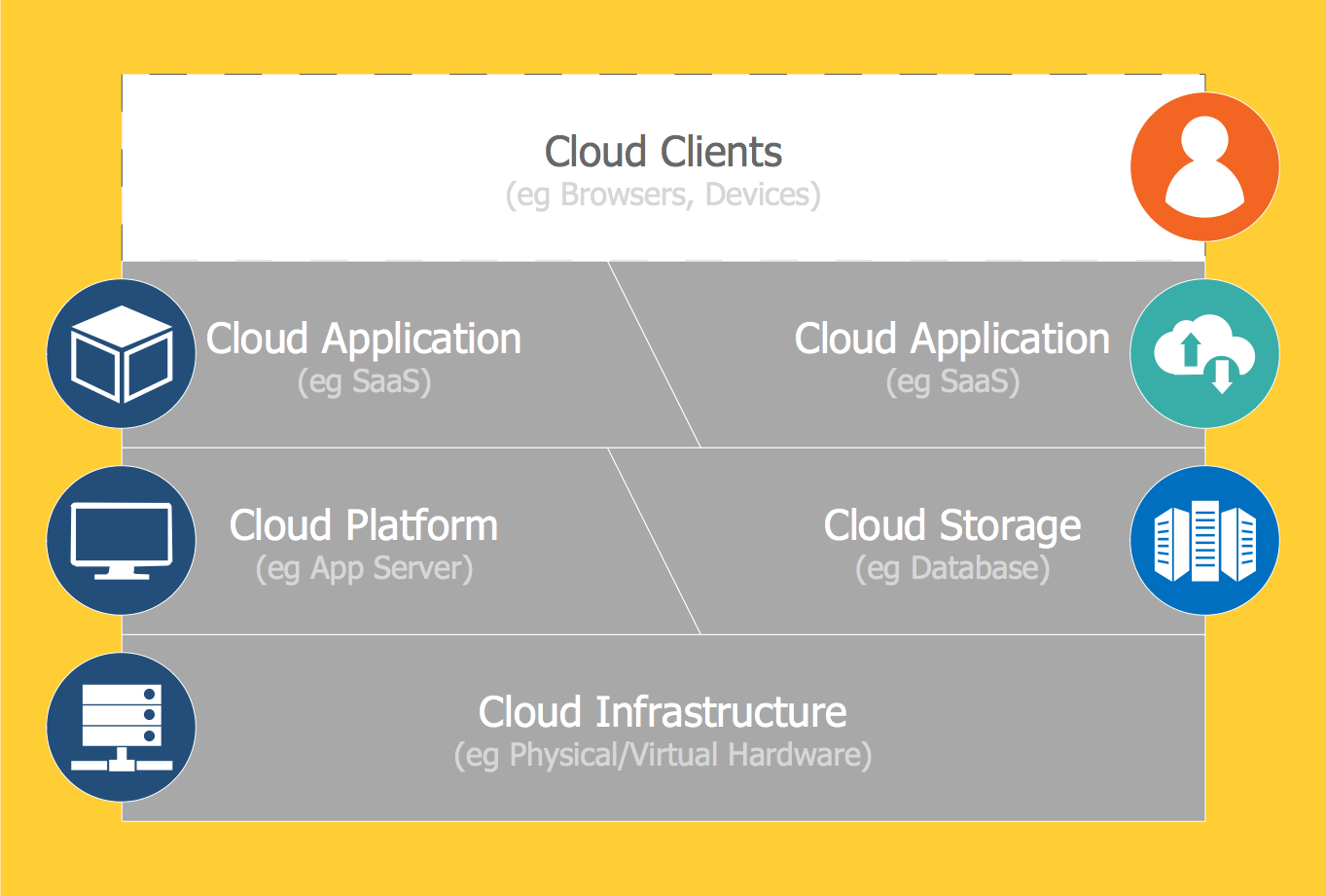
Introduction to Cloud Computing Architecture
The best way to visualize the introduction to Cloud computing architecture is to create diagrams and schematics representing what is a cloud computing and how it works. For their design, we recommend to use a powerful ConceptDraw PRO diagramming and vector drawing software supplied with Cloud Computing Diagrams solution from the Computers and Network area of ConceptDraw Solution ParkNetwork Icon
ConceptDraw PRO diagramming and vector drawing software extended with Computer Network Diagrams Solution from the Computer and Networks Area offers a set of useful tools, collection of templates, samples, and libraries of various computer symbols, computer devices icons, computer network icon for fast and easy drawing network computer diagrams and illustrations.- Camera layout schematic | Marketing Diagrams | Computers and ...
- Cyber Security Degrees | Network Security Devices | IT Security ...
- Cyber Security Degrees | IT Security Solutions | Network Security ...
- Cyber Security Degrees | | Network Security Diagrams | What Is ...
- | Cyber Security Degrees | | Computer Security Risk
- Network Security Devices | Network Security Tips | IT Security ...
- Health IT dashboard | EPC IT Solutions | NIH IT enterprise ...
- Design elements - Office | Office - Design Elements | Cisco Security ...
- Information Technology Cloud Computing
- Cloud Solutions Technology
- Enterprise Architecture Diagrams | Network Diagram Software ...
- Design elements - Cybersecurity round icons | Cyber Security ...
- How to Create a CCTV Diagram in ConceptDraw PRO | Security and ...
- Camera layout schematic | Security and Access Plans | How to ...
- Technology - Vector stencils library | Telecommunication networks ...
- Enterprise Architecture Diagrams | Network Diagram Software ...
- Network Security Model | Network Security | Secure Wireless ...
- Internet symbols - Vector stencils library | Access and security ...
- 4 Level pyramid model diagram - Information systems types | 5 Level ...
- Network Security | Network Security Model | ConceptDraw PRO ...