Storage area networks (SAN). Computer and Network Examples
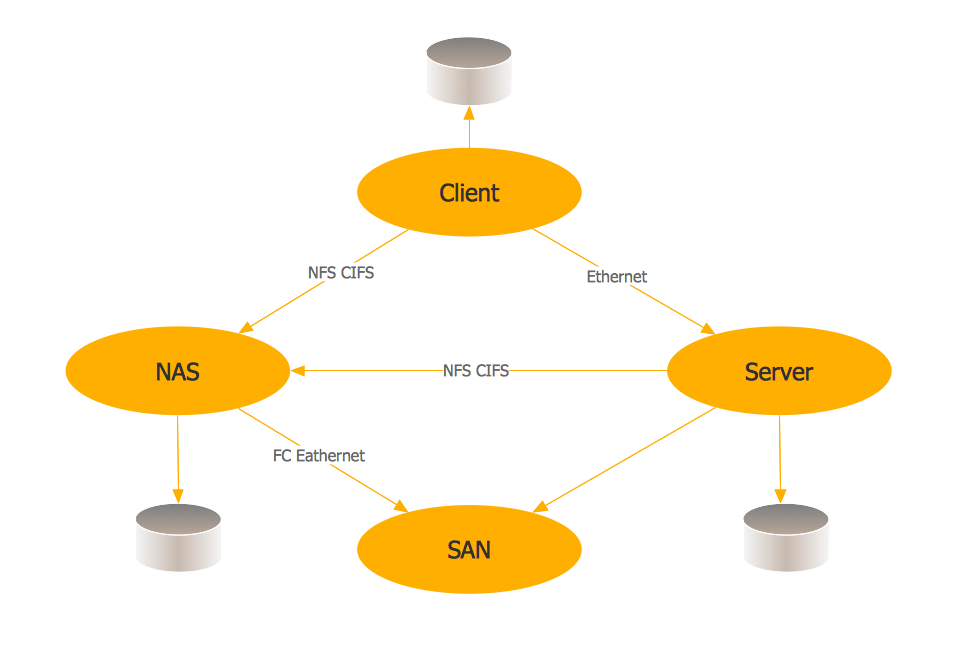
A Storage area network (SAN) is a dedicated network that provides access to data storage and operations only on the block level. SAN usually has own network of storage devices/elements and disk arrays that are connected with each other and to a remote data-sharing network. SANs are widely used for enhancing the storage devices (optical jukeboxes, disk arrays, tape libraries) that are accessible for networked servers. This example was created in ConceptDraw DIAGRAM using the Computer and Networks Area of ConceptDraw Solution Park. It shows the hybrid of Storage area network (SAN) and Network Attached Storage (NAS) technologies.
Daisy Chain Network Topology
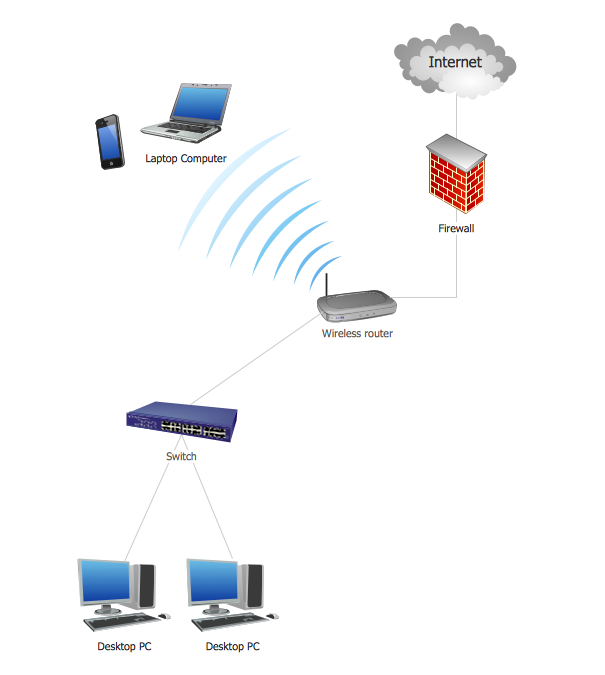
This sample was created in ConceptDraw DIAGRAM diagramming and vector drawing software using the Computer and Networks solution from Computer and Networks area of ConceptDraw Solution Park. A Daisy Chain is the simple computer network. It is the easiest way to add more Ethernet devices into the network. In the Daisy Chain network one computer is connected to the next without any intervening devices, thus the message is sent from one computer to the next and then to the next and so on. A Daisy Chain can be linear or ring
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors to help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics to share knowledge about effective ways of networks protection with help of software and network security devices of different cyber security degrees, Network Plans for secure wireless network, Computer Security Diagrams to visually tell about amazing possibilities of IT security solutions. The samples and examples reflect the power of ConceptDraw DIAGRAM software in drawing Network Security Diagrams, give the representation about variety of existing types of attacks and threats, help to realize their seriousness and the methods to deal with them.
Network Topology Illustration
ConceptDraw DIAGRAM is the best software for illustration the network topologies. It's very easy and quickly to design the network topology diagrams of any kinds and complexity in ConceptDraw DIAGRAM diagramming and vector drawing software using the Computer and Networks solution from Computer and Networks area of ConceptDraw Solution Park.
 AWS Architecture Diagrams
AWS Architecture Diagrams
AWS Architecture Diagrams with powerful drawing tools and numerous predesigned Amazon icons and AWS simple icons is the best for creation the AWS Architecture Diagrams, describing the use of Amazon Web Services or Amazon Cloud Services, their application for development and implementation the systems running on the AWS infrastructure. The multifarious samples give you the good understanding of AWS platform, its structure, services, resources and features, wide opportunities, advantages and benefits from their use; solution’s templates are essential and helpful when designing, description and implementing the AWS infrastructure-based systems. Use them in technical documentation, advertising and marketing materials, in specifications, presentation slides, whitepapers, datasheets, posters, etc.
 Block Diagrams
Block Diagrams
Block diagrams solution extends ConceptDraw DIAGRAM software with templates, samples and libraries of vector stencils for drawing the block diagrams.
Cisco Buildings. Cisco icons, shapes, stencils and symbols
Cisco icons are globally recognized and generally accepted as standard for network icon topologies. The ConceptDraw vector stencils library "Cisco buildings" contains 21 symbols for drawing the computer network diagrams using the ConceptDraw DIAGRAM diagramming and vector drawing software.
 Cisco Network Diagrams
Cisco Network Diagrams
Cisco Network Diagrams solution extends ConceptDraw DIAGRAM with the best characteristics of network diagramming software. Included samples, templates and libraries of built-in standardized vector Cisco network icons and Cisco symbols of computers, network devices, network appliances and other Cisco network equipment will help network engineers, network designers, network and system administrators, as well as other IT professionals and corporate IT departments to diagram efficiently the network infrastructure, to visualize computer networks topologies, to design Cisco computer networks, and to create professional-looking Cisco Computer network diagrams, Cisco network designs and schematics, Network maps, and Network topology diagrams in minutes.
HelpDesk
How to Create a Network Security Diagram
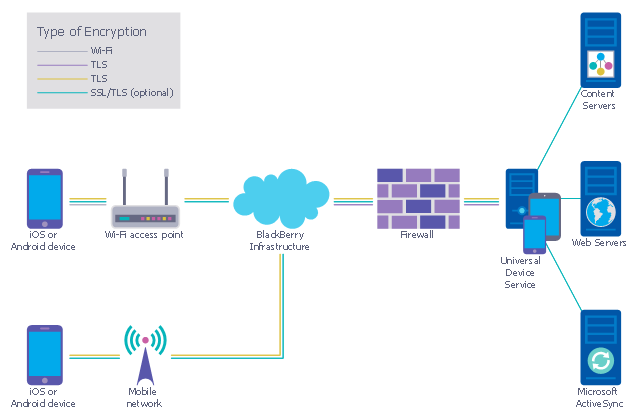
Network security requires constant work and attention to details. Each user, whether an individual or organization, owns a piece of information, considered to be valuable. The enforcement of network security, whether it be local network security, or wireless network security is the core for creating the secure environment of the daily working processes. Network security is accomplished through hardware and software. The network security system must be sophisticated and modern inside, but simple and understandable for the user. The visual scheme of a security system can be presented in the form of a Network Security diagram. ConceptDraw DIAGRAM provides the toolkit for network security system visualization with its Network Security Diagram solution.This example was designed on the base of the diagram from the "BYOD Guidance: BlackBerry Secure Work Space" on the website of the UK Communications Electronics Security Group (CESG).
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Secure Work Space (SWS) for iOS and Android is a containerisation, application-wrapping and secure connectivity option that delivers a higher level of control and security to iOS and Android devices, all managed through the BlackBerry Enterprise Service (BES) administration console.
Work space applications are secured and separated from personal applications and data. The work space applications include an integrated email, calendar, and contacts application, an enterprise-level secure browser, and a secure document viewing and editing application.
The work browser allows users to securely browse the organisation’s intranet and the Internet. If the device is lost or the employee leaves the organisation, you can chose to delete only corporate information or all information from the device.
...
Recommended network architecture
The walled garden architecture, shown below, aims to limit the impact of a compromise of an EUD and isolate high risk components from high value components where possible. The enterprise servers installed as part of SWS are high value resources that require suitable protection but are also high risk; they perform complex processing tasks that are more likely to contain exploitable vulnerabilities. These competing priorities make securely placing the servers into an existing network challenging, and organisations that wish to deviate from this architecture below should ensure they understand the risks of doing so."
[cesg.gov.uk/ guidance/ byod-guidance-blackberry-secure-work-space]
The cybersecurity diagram example "Recommended network architecture for BlackBerry SWS" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
 Computer Network Diagrams
Computer Network Diagrams
Computer Network Diagrams solution extends ConceptDraw DIAGRAM software with samples, templates and libraries of vector icons and objects of computer network devices and network components to help you create professional-looking Computer Network Diagrams, to plan simple home networks and complex computer network configurations for large buildings, to represent their schemes in a comprehensible graphical view, to document computer networks configurations, to depict the interactions between network's components, the used protocols and topologies, to represent physical and logical network structures, to compare visually different topologies and to depict their combinations, to represent in details the network structure with help of schemes, to study and analyze the network configurations, to communicate effectively to engineers, stakeholders and end-users, to track network working and troubleshoot, if necessary.
Network Topology Mapper
Network Topology in communication networks, a topology is a usually schematic description of the arrangement of a network, including its nodes and connecting lines. There are two ways of defining network geometry: the physical topology and the logical topology. Network Topology Mapper offers extensive drawing tools professional-looking network diagrams quickly and easily allowing you to clearly represent and communicate network architecture, topology, and design to engineers, stakeholders and end-users.Block Diagram
The vector stencils libraries: Block Diagrams, Blocks with Perspective, Callouts, Connectors, Raised Blocks from the solution Block Diagrams contain specific block diagram symbols such as arrows, input/output symbols, start/end symbols, processing symbols, conditional symbols, commenting symbols, callouts, connectors, etc. for ConceptDraw DIAGRAM diagramming and vector drawing software. The Block Diagrams solution is contained in a "Diagrams" area of ConceptDraw Solution Park. Use the libraries from the Block Diagrams solution to draw block diagrams for your business documents, presentations and websites in a few minutes.Star Network Topology
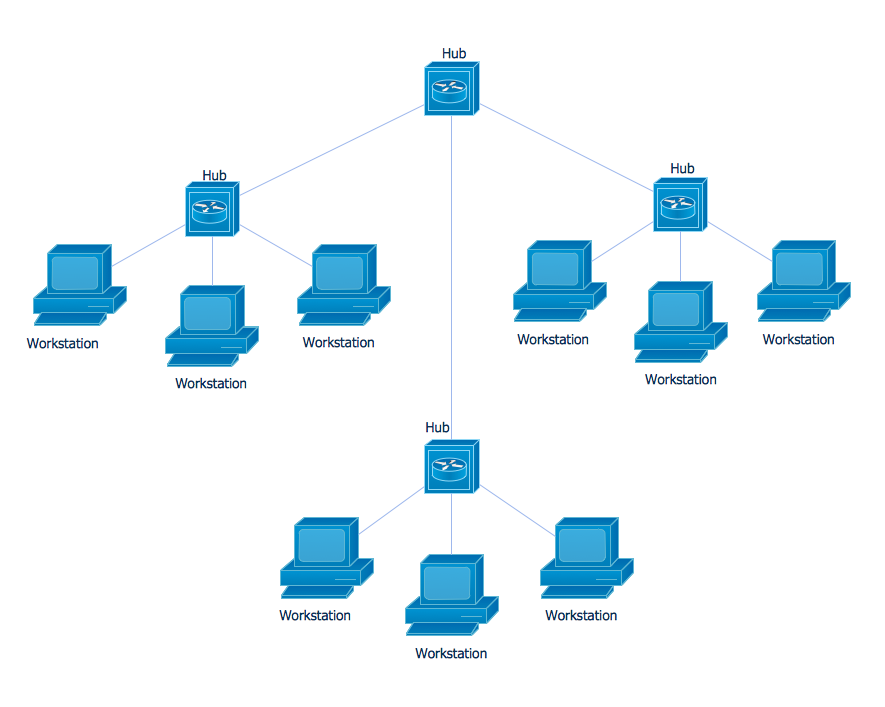
Star is a basic computer network topology in which all nodes (computers and peripheral devices) of the network are connected to the central hub or switch with a point-to-point connection, forming a physical network segment. Such network segment can function separately or as a part of complex network topology. The switch is a server, the peripherals are the clients. The large workload and functions of network management are entrusted on the central computer, all information exchange goes through it, so it must to be obligatory the most powerful. The star network topology is a simple topology for design and implementation. Its advantages are high performance, flexible administration capabilities, simplicity of adding additional nodes and search of faults, the fact that a failure of one workstation doesn't affect the work of entire network. But the failure of central hub will result the failure of whole network or network segment - it's the main disadvantage. Use the ConceptDraw DIAGRAM with Computer and Networks solution to designing Star Network Topology Diagrams fast and easy.
- AWS Architecture Diagrams | Block Diagrams | Interactive Voice ...
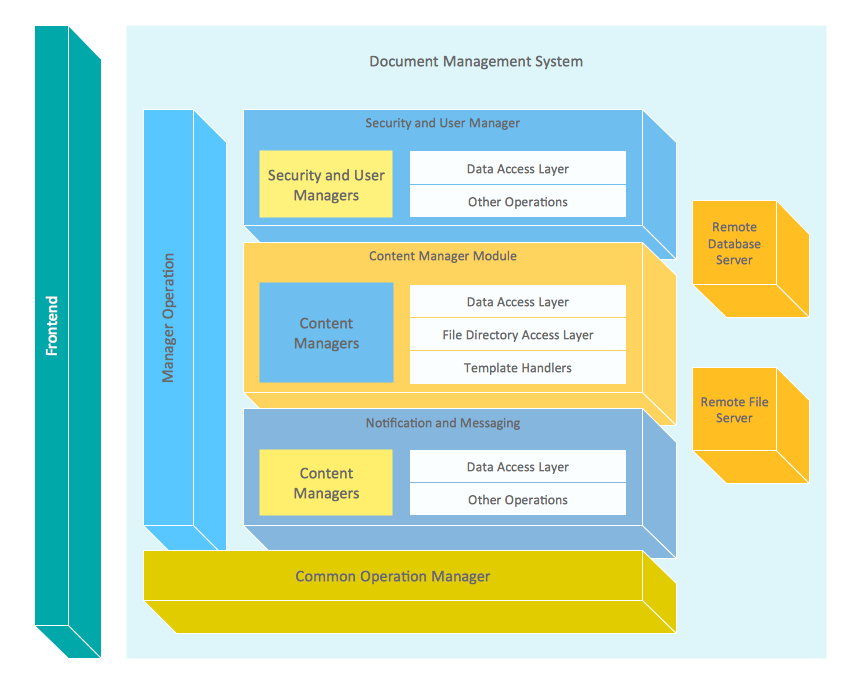
- Block diagram - Document management system architecture | How ...
- Network Topology Mapper | UML Block Diagram | Network ...
- Computer Network Diagrams | Simple Drawing Applications for Mac ...
- Enterprise Architecture Diagrams | How to Create an Enterprise ...
- Block diagram - Document management system architecture | Cisco ...
- Block Diagram Of Wired Lan
- Block Diagrams | AWS Architecture Diagrams | Types of Flowcharts ...
- Block Diagrams | Process Flowchart | How to Create a Computer ...
- Block Diagrams | Fault Tree Analysis Diagrams | Near-me area ...
- Example System Block Diagram Database Architecture
- Network Architecture | Storage area networks (SAN). Computer and ...
- Block diagram - Document management system architecture | Dms ...
- Enterprise Architecture Diagrams | AWS Architecture Diagrams ...
- Local area network (LAN). Computer and Network Examples ...
- Block Diagrams | AWS Architecture Diagrams | Data Flow Diagrams ...
- Block Diagram And Explanation Of Wifi Router
- Enterprise Architecture Diagrams | Storage area networks (SAN ...
- Network Security Diagrams | Storage area networks (SAN ...
- Network Block Diagram Examples