Active Directory Network. Computer and Network Examples
It’s quite a difficult task to manage the computer network today. But ConceptDraw PRO with Computer and Networks solution can help to the system and network administrators plan, create and support the work of their networks.
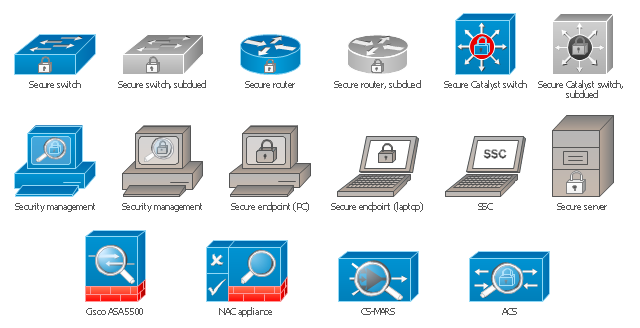
The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment for drawing Cisco computer network diagrams.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The symbols example "Cisco security - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ computer-networks-cisco
Network Security Model
Creation of well thought-out network security model will effectively help you in realization your network's security. ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park lets fast and easy design all variety of network security models: Open network security model, Closed network security model, Restrictive network access model.The vector stencils library "Cisco security" contains 16 symbols of security devices and equipment.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to create the Cisco computer network diagrams using the ConceptDraw PRO diagramming and vector drawing software.
"Network security consists of the provisions and policies adopted by a network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password." [Network security. Wikipedia]
The example "Design elements - Cisco routers" is included in the Cisco Network Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution enhances the ConceptDraw PRO v10 functionality with large collection of predesigned vector stencils of cybersecurity clipart, shapes, icons and connectors to help you succeed in designing professional and accurate Ne
Network Security Tips
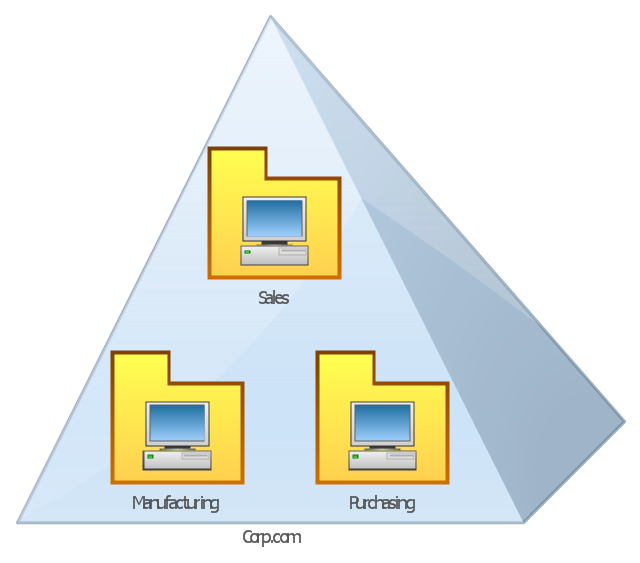
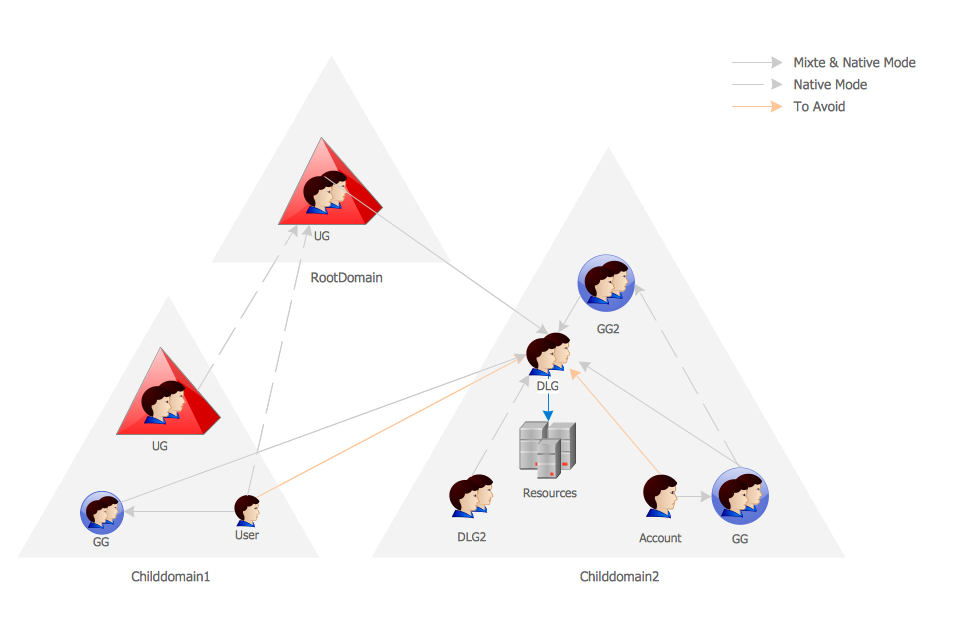
The Internet is a huge world with unlimited possibilities. But with all its numerous advantages, the Internet also conceals many dangers and security threats, that's why we advise you to follow simple network security tips. ConceptDraw PRO diagramming and vector drawing software supplied with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park is an ideal software for easy designing Network Security Diagrams and attractive illustrations with effective network security tips.This AD diagram example was redesigned from the picture "Single root domain with a structured OU model" from the book "Active Directory for Dummies".
"A domain is the cornerstone that you lay whenever you create trees and forests. Regardless of whether you design a tree or a forest, the starting point is always the root domain. The root domain is the first domain that you create in your AD structure, and it sits at the top of your diagram.
The root domain of your tree, similar to any other domain, is a grouping of
resources built on the following components:
(1) Domain controllers.
(2) Security policies. ...
For many small and medium-sized companies, a single root domain with a
structured OU (organizational unit) model... provides sufficient flexibility for an AD tree. ...
However, larger companies, companies with complex organization charts, and
companies with multiple sites often find that a single domain isn’t suitable." [Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "Single root domain with a structured OU model" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
"A domain is the cornerstone that you lay whenever you create trees and forests. Regardless of whether you design a tree or a forest, the starting point is always the root domain. The root domain is the first domain that you create in your AD structure, and it sits at the top of your diagram.
The root domain of your tree, similar to any other domain, is a grouping of
resources built on the following components:
(1) Domain controllers.
(2) Security policies. ...
For many small and medium-sized companies, a single root domain with a
structured OU (organizational unit) model... provides sufficient flexibility for an AD tree. ...
However, larger companies, companies with complex organization charts, and
companies with multiple sites often find that a single domain isn’t suitable." [Steve Clines and Marcia Loughry, Active Directory® For Dummies®, 2nd Edition. 2008]
The Active Directory diagram example "Single root domain with a structured OU model" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
HelpDesk
Download and Install ConceptDraw Office on your PC
You can use the following instruction to download and install ConceptDraw products for Windows . The download process is very simple due to the fact that all applications are bundled into the ConceptDraw Office suite. ConceptDraw Solution Browser is a download manager that is responsible for downloading, installing, uninstalling and updating of the ConceptDraw Office for Windows and associated solutions.HelpDesk
Download and Install ConceptDraw Office on Mac
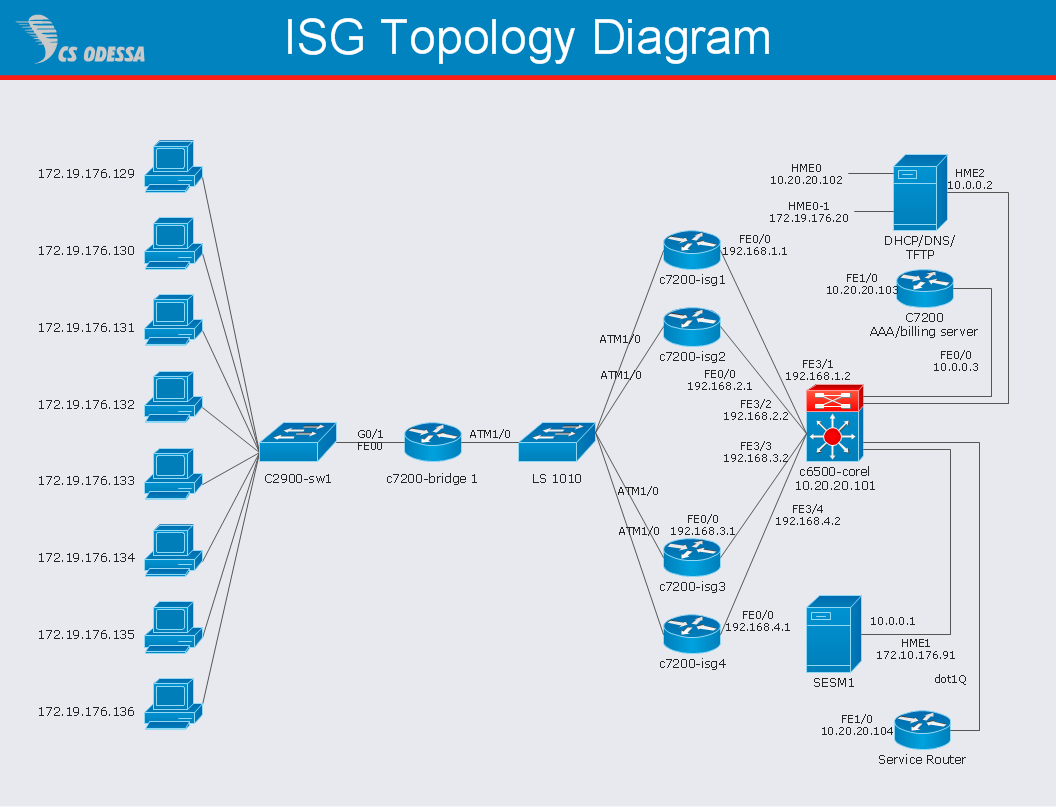
Find out how to download and install ConceptDraw software products for OS X on your computer. The download process is very simple due to the fact that all ConceptDraw applications are pooled into the ConceptDraw Office bundle. ConceptDraw Solution Browser is a download manager that is responsible for downloading, installing, uninstalling and updating of the ConceptDraw Office for Windows and associated solutions.Network Diagram Software ISG Network Diagram
Drawing ISG Network Diagram using ConceptDraw PRO stencils
 Bubble Diagrams
Bubble Diagrams
Bubble diagrams have enjoyed great success in software engineering, architecture, economics, medicine, landscape design, scientific and educational process, for ideas organization during brainstorming, for making business illustrations, presentations, planning, design, and strategy development. They are popular because of their simplicity and their powerful visual communication attributes.
 Block Diagrams
Block Diagrams
Block diagrams solution extends ConceptDraw PRO software with templates, samples and libraries of vector stencils for drawing the block diagrams.
The vector stencils library "Active Directory" contains 20 symbols of Active Directory elements for drawing AD network diagrams. It helps network and system administrators to visualize Microsoft Windows Active Directory structures for network design, installation and maintainance.
"An Active Directory structure is an arrangement of information about objects. The objects fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Security principals are assigned unique security identifiers (SIDs).
Each object represents a single entity - whether a user, a computer, a printer, or a group - and its attributes. Certain objects can contain other objects. An object is uniquely identified by its name and has a set of attributes - the characteristics and information that the object represents - defined by a schema, which also determines the kinds of objects that can be stored in Active Directory.
The schema object lets administrators extend or modify the schema when necessary. However, because each schema object is integral to the definition of Active Directory objects, deactivating or changing these objects can fundamentally change or disrupt a deployment. Schema changes automatically propagate throughout the system. Once created, an object can only be deactivated - not deleted. Changing the schema usually requires planning. Sites are implemented as a set of well-connected subnets." [Active Directory. Wikipedia]
The AD symbols example "Active Directory - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ active-directory-diagrams
"An Active Directory structure is an arrangement of information about objects. The objects fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Security principals are assigned unique security identifiers (SIDs).
Each object represents a single entity - whether a user, a computer, a printer, or a group - and its attributes. Certain objects can contain other objects. An object is uniquely identified by its name and has a set of attributes - the characteristics and information that the object represents - defined by a schema, which also determines the kinds of objects that can be stored in Active Directory.
The schema object lets administrators extend or modify the schema when necessary. However, because each schema object is integral to the definition of Active Directory objects, deactivating or changing these objects can fundamentally change or disrupt a deployment. Schema changes automatically propagate throughout the system. Once created, an object can only be deactivated - not deleted. Changing the schema usually requires planning. Sites are implemented as a set of well-connected subnets." [Active Directory. Wikipedia]
The AD symbols example "Active Directory - Vector stencils library" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Active Directory Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
www.conceptdraw.com/ solution-park/ active-directory-diagrams
- ConceptDraw PRO Network Diagram Tool | Network Security ...
- Network Security . Computer and Network Examples | Cisco security ...
- Cisco security - Vector stencils library
- Cisco Security . Cisco icons, shapes, stencils and symbols | Cisco ...
- Project — Assigning Resources | Advanced Resource Assignment ...
- Security Management
- Cisco Network Design. Cisco icons, shapes, stencils, symbols and ...
- Cisco Routers. Cisco icons, shapes, stencils and symbols | Cisco ...
- Active Directory Diagram | Network Diagramming Software for ...
- Domain Network Diagrams
- Active Directory Domain Services | Active Directory Diagram | Single ...
- Account Flowchart. Flowchart Examples | Budgeted appropriations ...
- How to Draw a Security and Access Floor Plan | Safety and Security ...
- Active Directory Diagram | Active Directory Domain Services | Single ...
- Organizational Units | Network Diagramming Software for Network ...
- Security and Access Plans | How to Draw a Security and Access ...
- Single root domain with a structured OU model | Active Directory ...
- Enterprise private network | EPN Frame-Relay and Dial-up Network ...
- Network layout floorplan - Vector stencils library | Single root domain ...
- Active Directory Diagram | Network Diagramming Software for ...





-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)
-cisco-security---vector-stencils-library.png--diagram-flowchart-example.png)