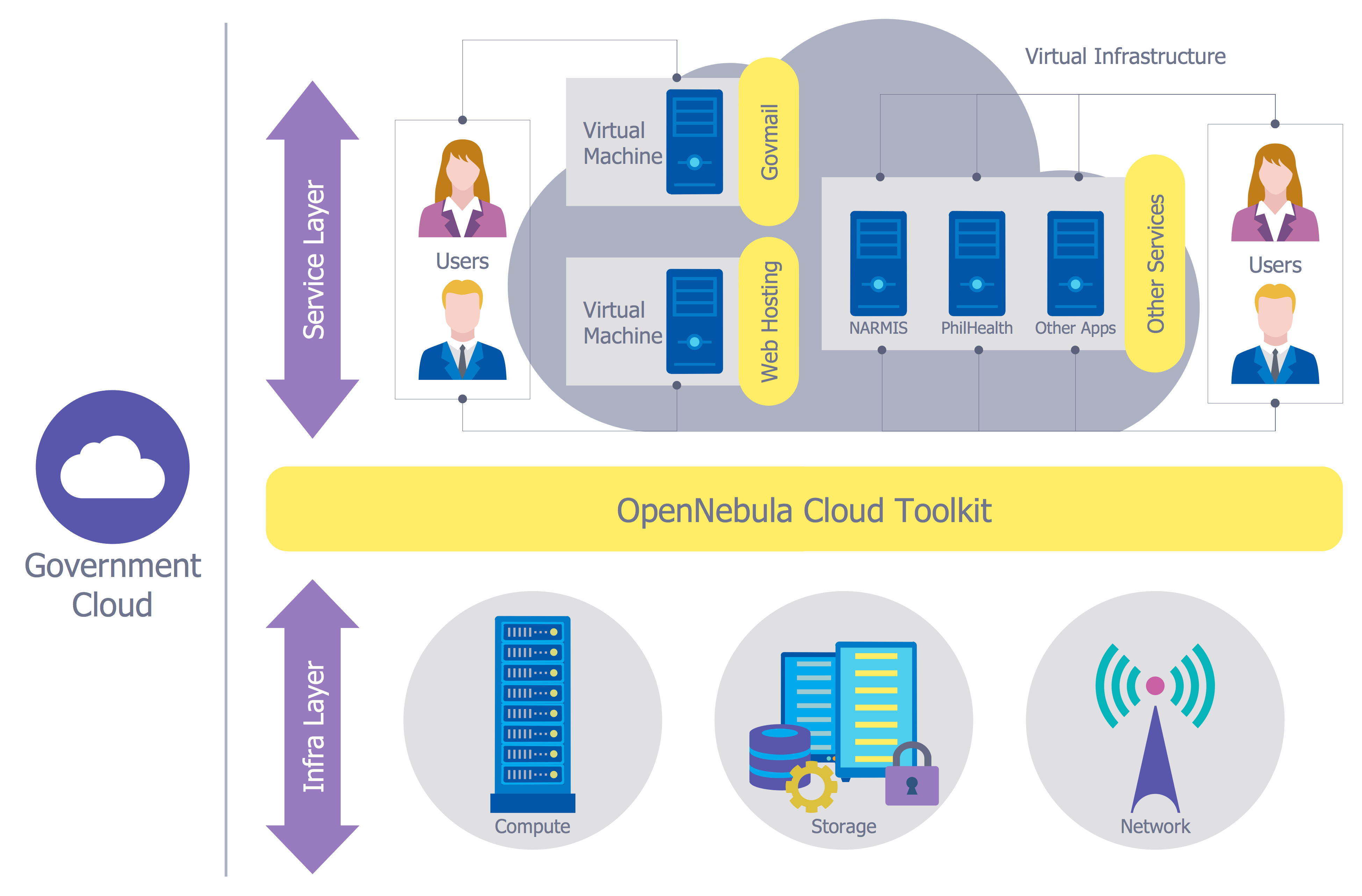
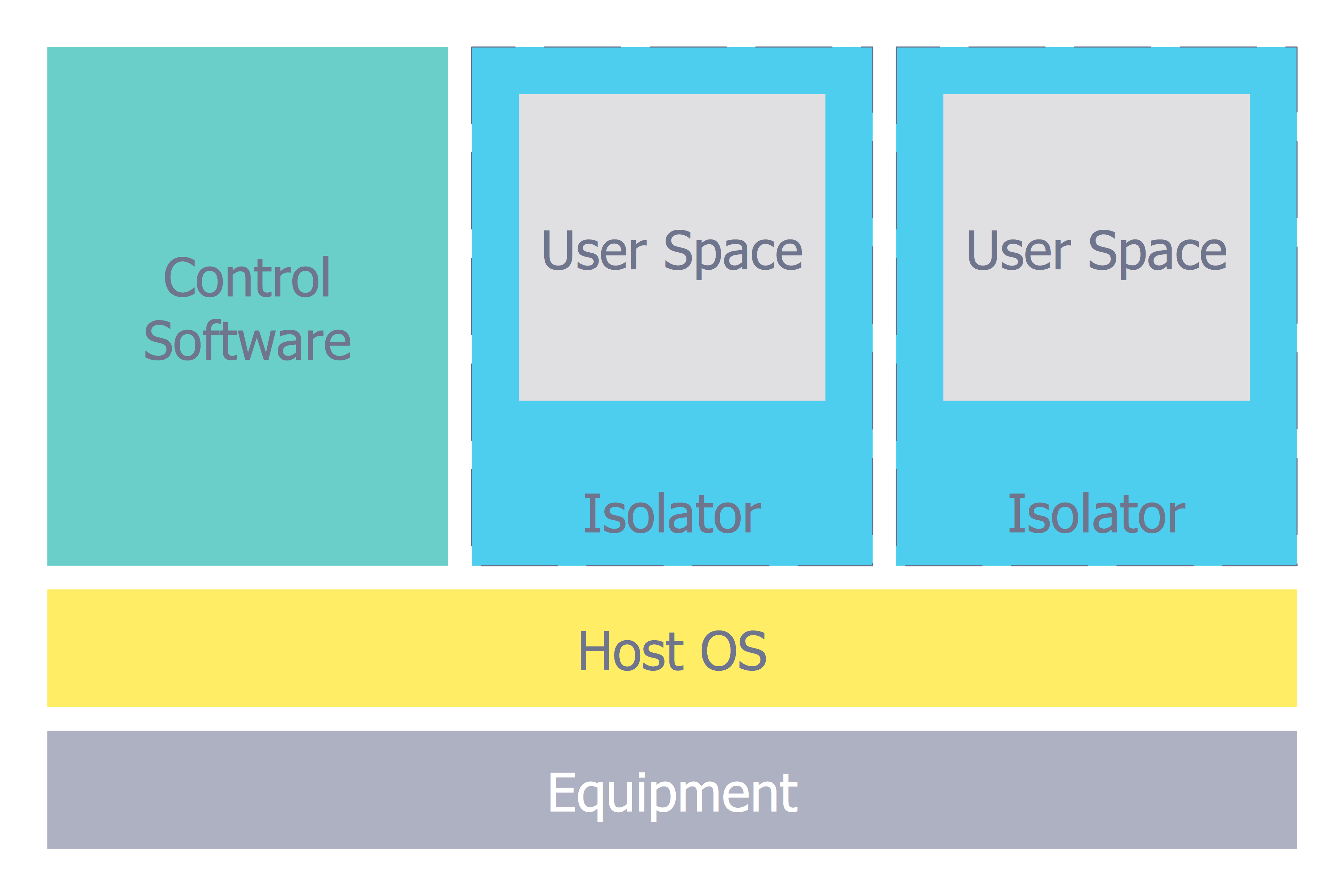
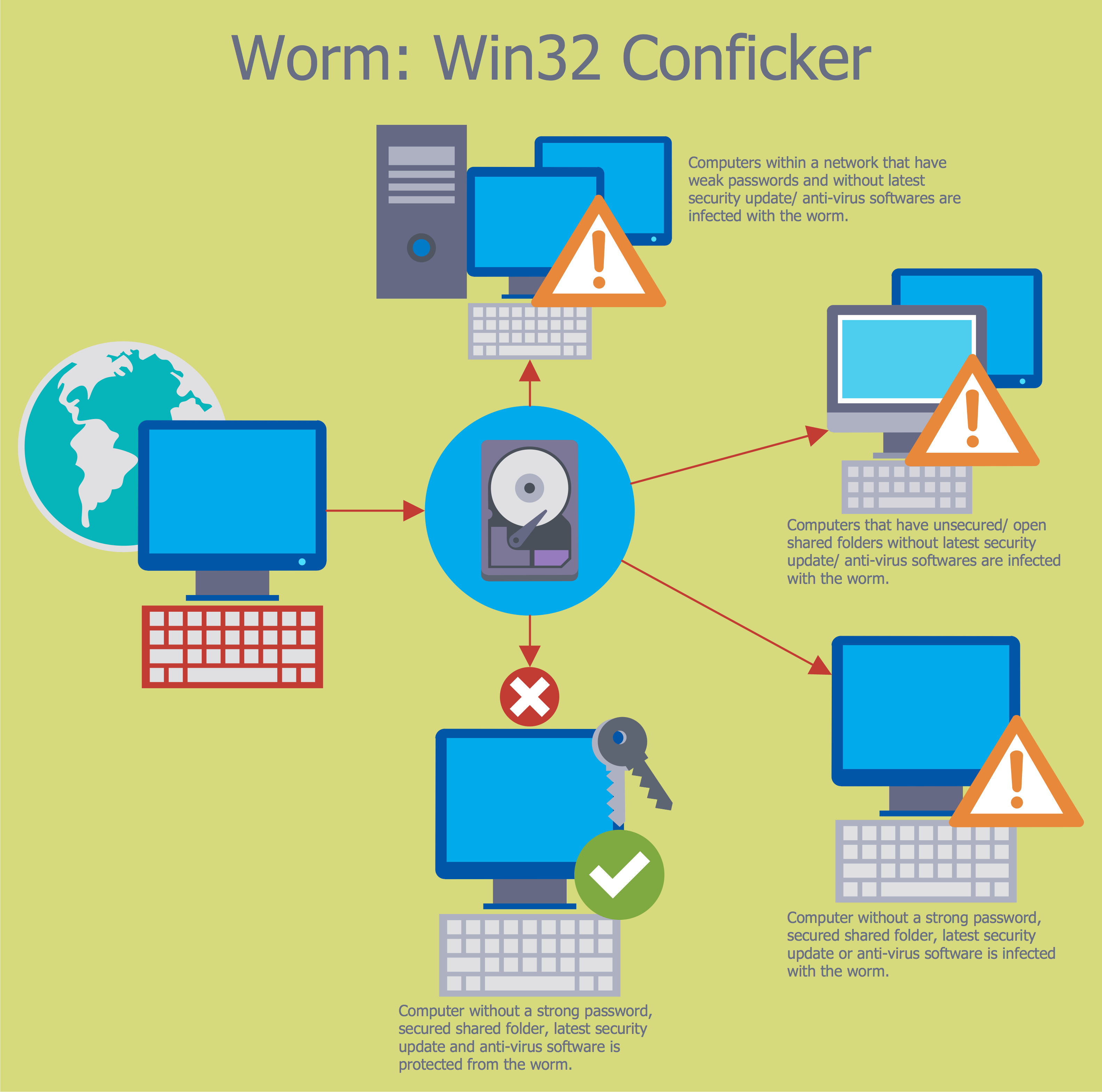
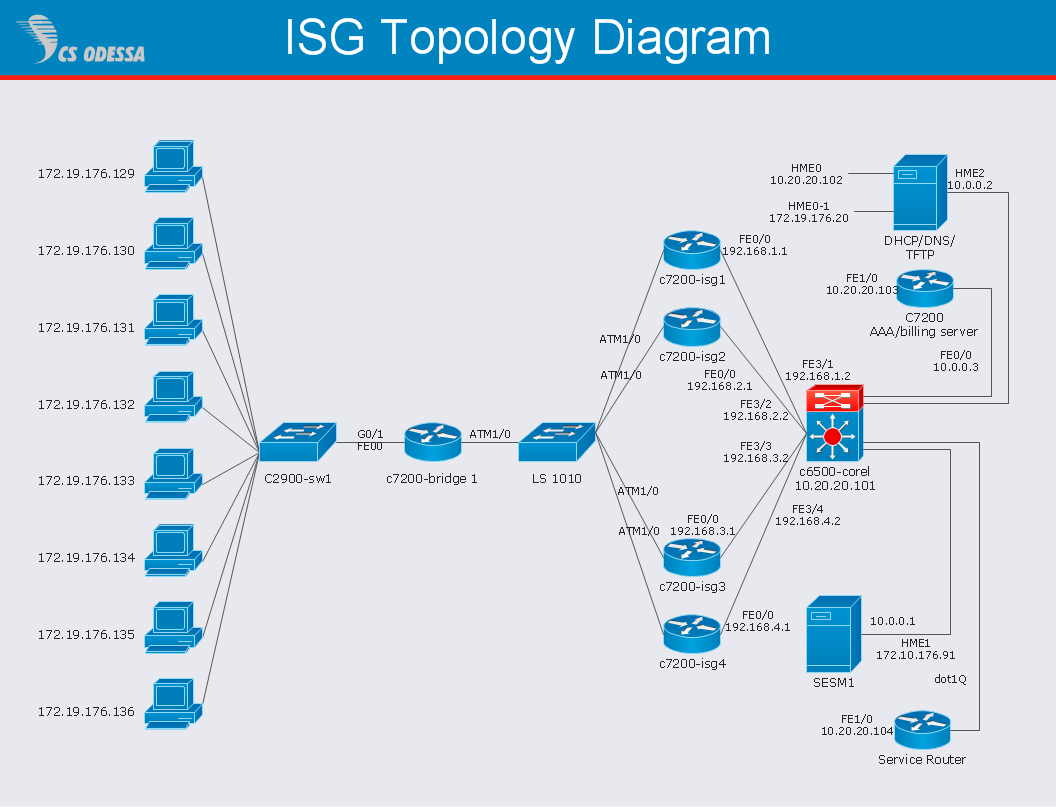
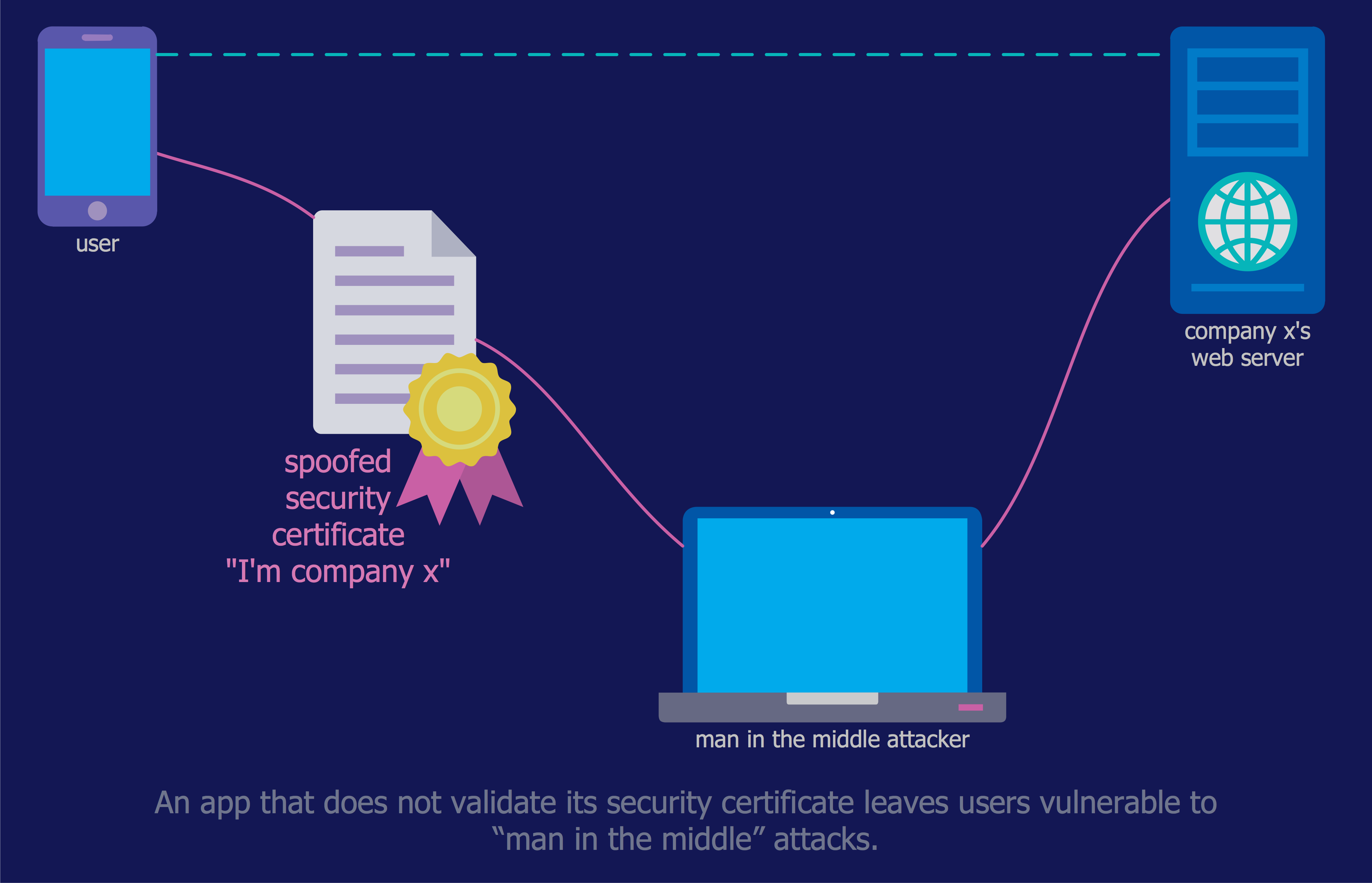
Network Security Model
Creation of well thought-out network security model will effectively help you in realization your network's security. ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park lets fast and easy design all variety of network security models: Open network security model, Closed network security model, Restrictive network access model.
 Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution enhances the ConceptDraw PRO v10 functionality with large collection of predesigned vector stencils of cybersecurity clipart, shapes, icons and connectors to help you succeed in designing professional and accurate Ne
Network Security Architecture Diagram
Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and hardware devices. You dream to find powerful software for easy designing Network Security Architecture Diagram? We recommend to use ConceptDraw PRO extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.
 Bubble Diagrams
Bubble Diagrams
Bubble diagrams have enjoyed great success in software engineering, architecture, economics, medicine, landscape design, scientific and educational process, for ideas organization during brainstorming, for making business illustrations, presentations, planning, design, and strategy development. They are popular because of their simplicity and their powerful visual communication attributes.
Network Security
The Internet is a giant computer network which connects computers all over the world. It is integral part of human society and business. But the serious question for network engineers, designers, lawmakers and enforcers is the need for protect the Internet networks from the Internet crimes, hacking and attacks. There are quite a number of hardware, software and physical methods of protection against them. The samples you see on this page were created in ConceptDraw PRO using the tools of Network Security Diagrams Solution for ConceptDraw PRO software. They show protection networks with Firewalls and other network security devices.Network Security Tips
The Internet is a huge world with unlimited possibilities. But with all its numerous advantages, the Internet also conceals many dangers and security threats, that's why we advise you to follow simple network security tips. ConceptDraw PRO diagramming and vector drawing software supplied with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park is an ideal software for easy designing Network Security Diagrams and attractive illustrations with effective network security tips.
 Fishbone Diagrams
Fishbone Diagrams
The Fishbone Diagrams solution extends ConceptDraw PRO v10 software with the ability to easily draw the Fishbone Diagrams (Ishikawa Diagrams) to clearly see the cause and effect analysis and also problem solving. The vector graphic diagrams produced using this solution can be used in whitepapers, presentations, datasheets, posters, and published technical material.
 Block Diagrams
Block Diagrams
Block diagrams solution extends ConceptDraw PRO software with templates, samples and libraries of vector stencils for drawing the block diagrams.
IT Security Solutions
Dynamic of development computer and network technologies increases the need in modern cyber security strategies and IT security solutions to support security of your data, to ensure data privacy, and to protect your operations from the cyber threats. Thanks to the Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park, the ConceptDraw PRO diagramming and vector drawing software is one of the unique IT security solutions for professional designing Network Security Diagrams.The vector stencils library "AWS Security, Identity and Compliance" contains 23 Amazon Web Services security, identity and compliance icons.
Use it to draw AWS architecture diagrams with ConceptDraw PRO software.
Amazon Security, Identity and Compliance services includes: "Amazon Cloud Directory (Create flexible cloud-native directories), AWS Identity & Access Management (Manage User Access and Encryption Keys), Amazon Inspector (Analyze Application Security), AWS Certificate Manager (Provision, Manage, and Deploy SSL/ TLS Certificates), AWS CloudHSM (Hardware-based Key Storage for Regulatory Compliance), AWS Directory Service (Host and Manage Active Directory), AWS Key Management Service (Managed Creation and Control of Encryption Keys), AWS Organizations (Policy-based management for multiple AWS accounts), AWS Shield (DDoS Protection), AWS WAF (Filter Malicious Web Traffic)" [aws.amazon.com]
The AWS icons example "Design elements - AWS Security, Identity and Compliance" is included in the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to draw AWS architecture diagrams with ConceptDraw PRO software.
Amazon Security, Identity and Compliance services includes: "Amazon Cloud Directory (Create flexible cloud-native directories), AWS Identity & Access Management (Manage User Access and Encryption Keys), Amazon Inspector (Analyze Application Security), AWS Certificate Manager (Provision, Manage, and Deploy SSL/ TLS Certificates), AWS CloudHSM (Hardware-based Key Storage for Regulatory Compliance), AWS Directory Service (Host and Manage Active Directory), AWS Key Management Service (Managed Creation and Control of Encryption Keys), AWS Organizations (Policy-based management for multiple AWS accounts), AWS Shield (DDoS Protection), AWS WAF (Filter Malicious Web Traffic)" [aws.amazon.com]
The AWS icons example "Design elements - AWS Security, Identity and Compliance" is included in the AWS Architecture Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Cyber Security Degrees
For protection various cyber environments are developed and applied large variety of cyber security standards, techniques, security concepts and approaches with different cyber security degrees. The ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park offers the number of useful tools which will help network security engineers, cyber security specialists, network and computer analysts easily and visually depict the knowledge and skills for research and prevention of intrusions, about protection critical information and analysis of cyber incidents, and for how to assess threats and vulnerabilities.
 Circular Arrows Diagrams
Circular Arrows Diagrams
Circular Arrows Diagrams solution extends ConceptDraw PRO v10 with extensive drawing tools, predesigned samples, Circular flow diagram template for quick start, and a library of ready circular arrow vector stencils for drawing Circular Arrow Diagrams, Segmented Cycle Diagrams, and Circular Flow Diagrams. The elements in this solution help managers, analysts, business advisers, marketing experts, scientists, lecturers, and other knowledge workers in their daily work.
 Workflow Diagrams
Workflow Diagrams
Workflow Diagrams solution extends ConceptDraw PRO software with samples, templates and vector stencils library for drawing the work process flowcharts.
HelpDesk
Download and Install ConceptDraw Office on your PC
You can use the following instruction to download and install ConceptDraw products for Windows . The download process is very simple due to the fact that all applications are bundled into the ConceptDraw Office suite. ConceptDraw STORE is a download manager that is responsible for downloading, installing, uninstalling and updating of the ConceptDraw Office for Windows and associated solutions.- Security Policy And Block Diagram
- Computer Security Policy
- Network Security Model | Network Security Diagrams | Network ...
- Block Diagram Of Security Policy And Other Diagram
- Organizational Units | Active Directory Diagrams | Active Directory ...
- EFS Operation | Gpo Flow Chart
- It Security Policy
- Group Policy Diagram Windows
- Firewall Policy Service Diagram
- Diagrams Of Business Policy
- Restrictive Security Model Diagram With Explaination
- Diagram On Purpose In Business Policy
- Fishbone Diagram Provider Policies
- Fishbone Diagrams | Fishbone Diagram | Security and Access Plans ...
- Flow Chart Of Policy Management
- Computer Security Diagram
- Microsoft Group Policy Diagram
- Network Security Diagrams | Daisy Chain Network Topology | Fork ...
- Business Policy Diagrams