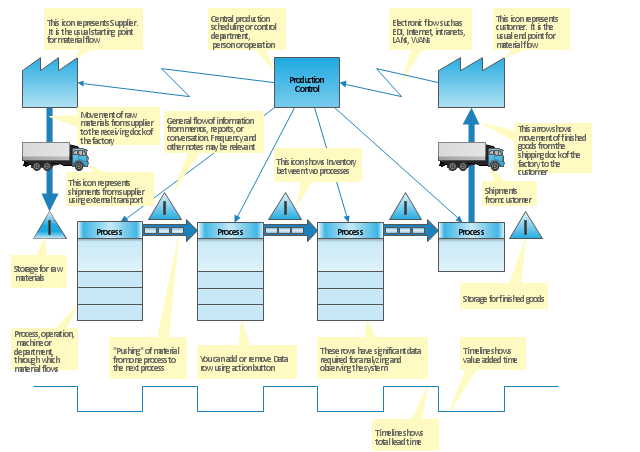
"Value stream mapping is a lean management principle used to analyze and design the flow of materials and information required to bring a product or service to a consumer. Pioneered by Henry Ford in the 1920s, perfected by Toyota. At Toyota, it is known as "material and information flow mapping". It can be applied to nearly any value chain. ...
Value stream mapping has supporting methods that are often used in Lean environments to analyze and design flows at the system level (across multiple processes).
Although value stream mapping is often associated with manufacturing, it is also used in logistics, supply chain, service related industries, healthcare, software development, product development, and administrative and office processes." [Value stream mapping. Wikipedia]
This value stream map template explains the meanings of the VSM design elements.
This Value stream map template for the ConceptDraw PRO diagramming and vector drawing software is included in the Value Stream Mapping solution from the Quality area of ConceptDraw Solution Park.
Value stream mapping has supporting methods that are often used in Lean environments to analyze and design flows at the system level (across multiple processes).
Although value stream mapping is often associated with manufacturing, it is also used in logistics, supply chain, service related industries, healthcare, software development, product development, and administrative and office processes." [Value stream mapping. Wikipedia]
This value stream map template explains the meanings of the VSM design elements.
This Value stream map template for the ConceptDraw PRO diagramming and vector drawing software is included in the Value Stream Mapping solution from the Quality area of ConceptDraw Solution Park.
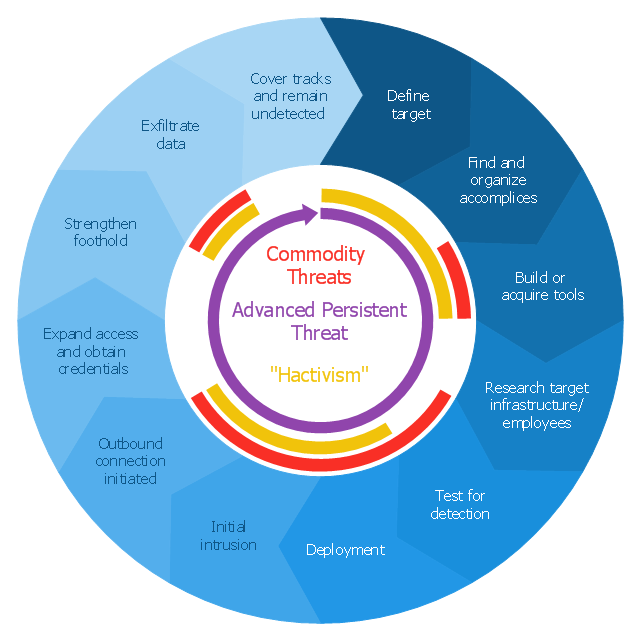
This circular arrows diagram sample shows advanced persistent threat lifecycle.
It was designed on the base of the Wikimedia Commons file: Advanced persistent threat lifecycle.jpg.
[commons.wikimedia.org/ wiki/ File:Advanced_ persistent_ threat_ lifecycle.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"Advanced Persistent Threat (APT) APT is a set of stealthy and continuous hacking processes often orchestrated by human targeting a specific entity. APT usually targets organizations and or nations for business or political motives. APT processes require high degree of covertness over a long period of time. As the name implies, APT consists of three major components/ processes: advanced, persistent, and threat. The advanced process signifies sophisticated techniques using malware to exploit vulnerabilities in systems. The persistent process suggests that an external command and control is continuously monitoring and extracting data off a specific target. The threat process indicates human involvement in orchestrating the attack.
APT usually refers to a group, such as a government, with both the capability and the intent to persistently and effectively target a specific entity. The term is commonly used to refer to cyber threats, in particular that of Internet-enabled espionage using a variety of intelligence gathering techniques to access sensitive information, but applies equally to other threats such as that of traditional espionage or attack. Other recognized attack vectors include infected media, supply chain compromise, and social engineering. Individuals, such as an individual hacker, are not usually referred to as an APT as they rarely have the resources to be both advanced and persistent even if they are intent on gaining access to, or attacking, a specific target." [Advanced persistent threat. Wikipedia]
The arrow donut chart example
"Advanced persistent threat lifecycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Circular Arrows Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
It was designed on the base of the Wikimedia Commons file: Advanced persistent threat lifecycle.jpg.
[commons.wikimedia.org/ wiki/ File:Advanced_ persistent_ threat_ lifecycle.jpg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"Advanced Persistent Threat (APT) APT is a set of stealthy and continuous hacking processes often orchestrated by human targeting a specific entity. APT usually targets organizations and or nations for business or political motives. APT processes require high degree of covertness over a long period of time. As the name implies, APT consists of three major components/ processes: advanced, persistent, and threat. The advanced process signifies sophisticated techniques using malware to exploit vulnerabilities in systems. The persistent process suggests that an external command and control is continuously monitoring and extracting data off a specific target. The threat process indicates human involvement in orchestrating the attack.
APT usually refers to a group, such as a government, with both the capability and the intent to persistently and effectively target a specific entity. The term is commonly used to refer to cyber threats, in particular that of Internet-enabled espionage using a variety of intelligence gathering techniques to access sensitive information, but applies equally to other threats such as that of traditional espionage or attack. Other recognized attack vectors include infected media, supply chain compromise, and social engineering. Individuals, such as an individual hacker, are not usually referred to as an APT as they rarely have the resources to be both advanced and persistent even if they are intent on gaining access to, or attacking, a specific target." [Advanced persistent threat. Wikipedia]
The arrow donut chart example
"Advanced persistent threat lifecycle" was created using the ConceptDraw PRO diagramming and vector drawing software extended with the Circular Arrows Diagrams solution from the area "What is a Diagram" of ConceptDraw Solution Park.
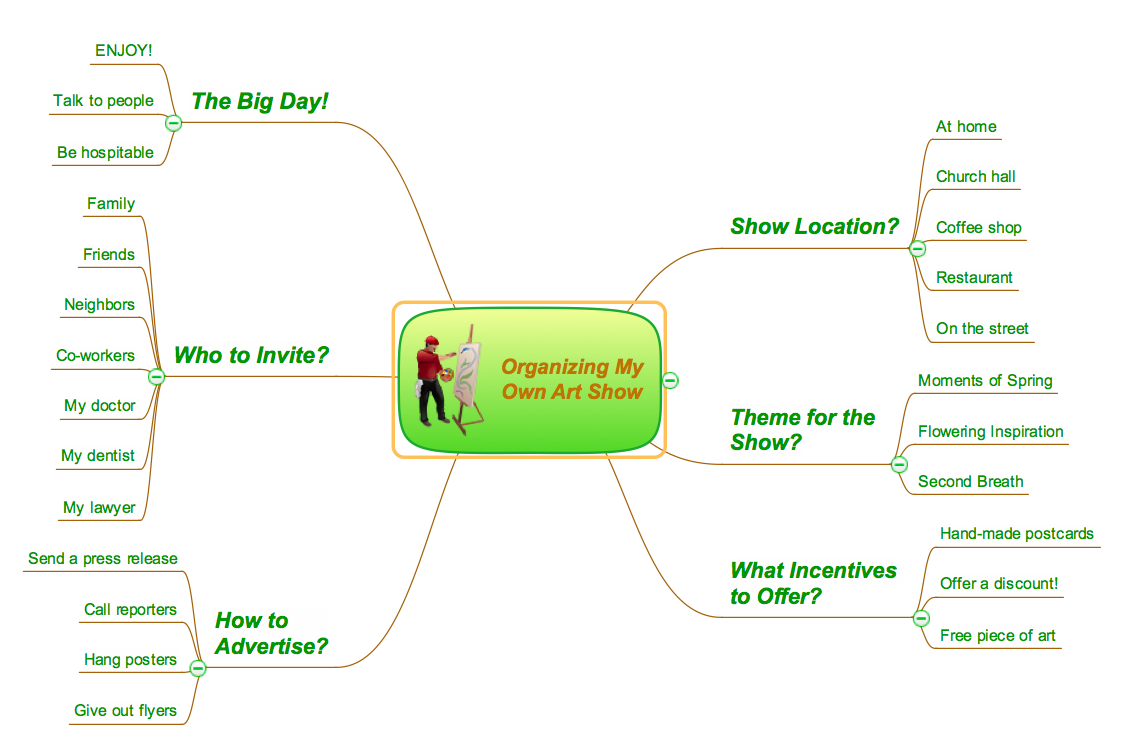
Think. Act. Accomplish.
ConceptDraw MINDMAP is ready to provide you with mind mapping tool which can serve as comprehensive productivity tool for your business.
 Entity-Relationship Diagram (ERD)
Entity-Relationship Diagram (ERD)
Entity-Relationship Diagram (ERD) solution extends ConceptDraw PRO software with templates, samples and libraries of vector stencils from drawing the ER-diagrams by Chen's and crow’s foot notations.
 Plumbing and Piping Plans
Plumbing and Piping Plans
Plumbing and Piping Plans solution extends ConceptDraw PRO v10.2.2 software with samples, templates and libraries of pipes, plumbing, and valves design elements for developing of water and plumbing systems, and for drawing Plumbing plan, Piping plan, PVC Pipe plan, PVC Pipe furniture plan, Plumbing layout plan, Plumbing floor plan, Half pipe plans, Pipe bender plans.
HelpDesk
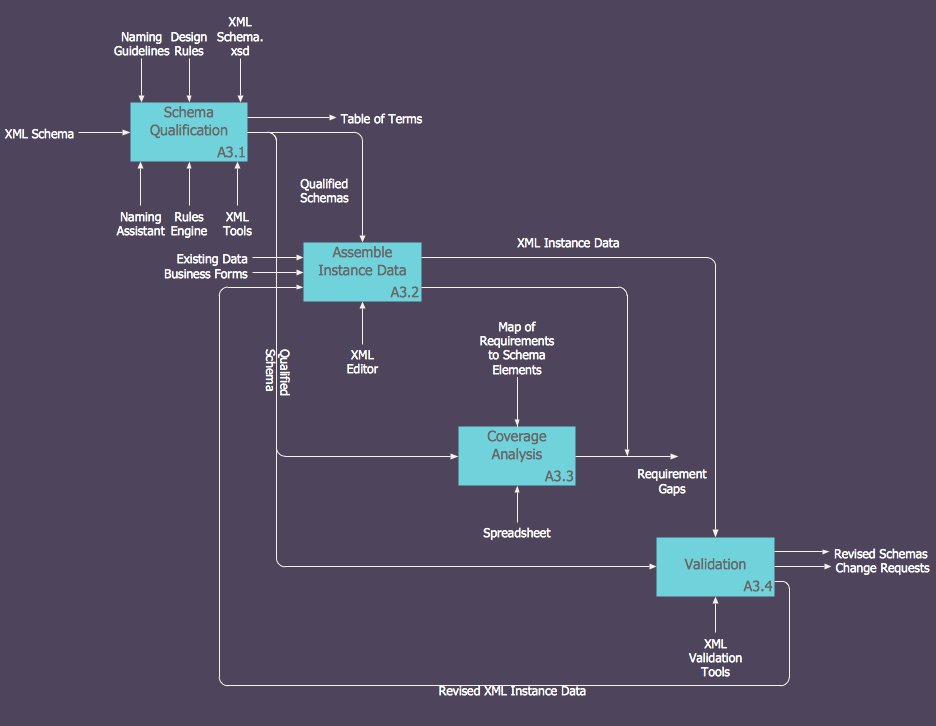
How to Create an IDEF0 Diagram for an Application Development
IDEF0 methods are intended to model the functions of a process, creating a graphical model that displays: what controls the function, who makes it, what resources are used and how they are connected with other functions. The IDEF0 tool is used to model the decisions, actions, and activities of a software system during the development process . IDEF0 diagram graphically depicts a model of a desired version of the application. ConceptDraw PRO allows you to create and communicate the IDEF0 diagrams of any complexity.
 Office Layout Plans
Office Layout Plans
Office layouts and office plans are a special category of building plans and are often an obligatory requirement for precise and correct construction, design and exploitation office premises and business buildings. Designers and architects strive to make office plans and office floor plans simple and accurate, but at the same time unique, elegant, creative, and even extraordinary to easily increase the effectiveness of the work while attracting a large number of clients.
- Supply Chain Process Flow Chart Templates
- Supply Chain Order Process Flow Chart Template
- Supply Chain Business Process Flow Diagram
- Mporters Supply Chain Diagram
- Supply Chain And Supply Chain Management
- Supply Chain Flow Chart Template
- Supply Chain Matrix Template
- Porter's value chain diagram - Template
- Value Chain In Plumbing
- Quality Supply Chain
- Quality In Supply Chain
- Event-driven Process Chain Diagrams | Pie Charts | Structured ...
- Quality Management In Supply Chain
- Supply Chain Process Management
- Supply Flow Chart
- Porter's value chain matrix diagram
- Value Stream Mapping Template
- Flow Chart Showing The Chain Of Customer Service In My Business
- How To Make Dfd Diagram Of Supplier Chain Management