Network Security Diagrams
Network Security Diagrams
The Network Security Diagrams solution enhances the ConceptDraw PRO v10 functionality with large collection of predesigned vector stencils of cybersecurity clipart, shapes, icons and connectors to help you succeed in designing professional and accurate Ne
Network Security
The Internet is a giant computer network which connects computers all over the world. It is integral part of human society and business. But the serious question for network engineers, designers, lawmakers and enforcers is the need for protect the Internet networks from the Internet crimes, hacking and attacks. There are quite a number of hardware, software and physical methods of protection against them.The samples you see on this page were created in ConceptDraw PRO using the tools of Network Security Diagrams Solution for ConceptDraw PRO software. They show protection networks with Firewalls and other network security devices.
The vector stencils library "Cybersecurity clipart" contains 197 computer security icons.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"Computer security, also known as cybersecurity or IT security, is the protection of information systems from theft or damage to the hardware, the software, and to the information on them, as well as from disruption or misdirection of the services they provide. It includes controlling physical access to the hardware, as well as protecting against harm that may come via network access, data and code injection, and due to malpractice by operators, whether intentional, accidental, or due to them being tricked into deviating from secure procedures." [Computer security. Wikipedia]
The icon set example "Design elements - Cybersecurity clipart" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
Use it to design your computer security diagrams and cybersecurity infographics with ConceptDraw PRO software.
"Computer security, also known as cybersecurity or IT security, is the protection of information systems from theft or damage to the hardware, the software, and to the information on them, as well as from disruption or misdirection of the services they provide. It includes controlling physical access to the hardware, as well as protecting against harm that may come via network access, data and code injection, and due to malpractice by operators, whether intentional, accidental, or due to them being tricked into deviating from secure procedures." [Computer security. Wikipedia]
The icon set example "Design elements - Cybersecurity clipart" is included in the Network Security Diagrams solution from the Computer and Networks area of ConceptDraw Solution Park.
HelpDesk
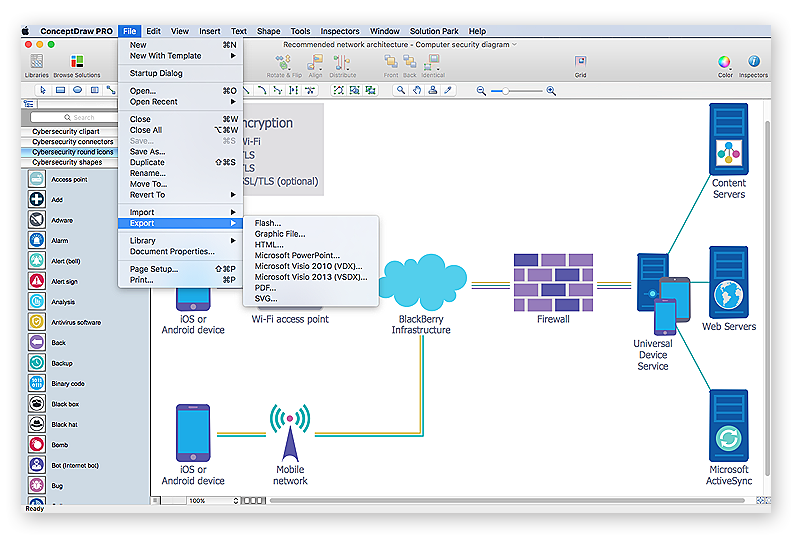
How to Create a Network Security Diagram Using ConceptDraw PRO
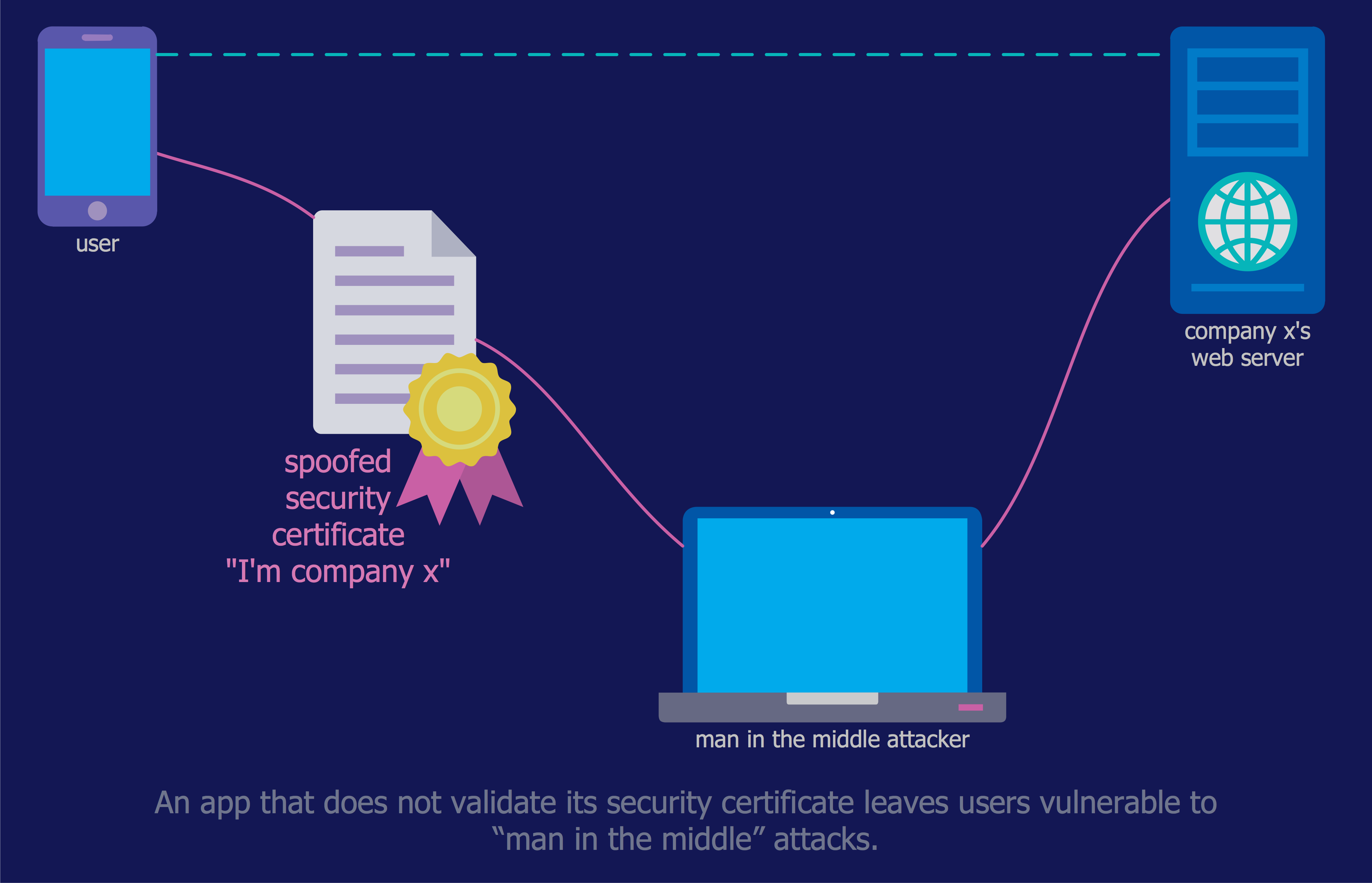
Network security requires constant work and attention to details. Each user, whether an individual or organization, owns an information, considered to be valuable. The enforcement of network security, whether it be a local network security, or wireless network security is core for creating the secure environment of the daily working processes. Network security is accomplished through hardware and software. Network security system must be sophisticated and modern inside, but simple and understandable for the user. The visual scheme of security system can be presented in the form of a Network Security diagram. ConceptDraw PRO provides the toolkit for network security system visualization with its Network Security Diagram solution.This example was designed on the base of the diagram from the article "How secure is that mobile app?" by N.V. Fleming on the website of the U.S. Federal Trade Commission (FTC).
"Neither company validated security certificates to make sure the app was sending the information to the right place. That left users vulnerable to “man in the middle attacks.” An attacker could trick the app into letting him access communications between the app and the online service. Neither the person using the app nor the online service would know the attacker was there." [consumer.ftc.gov/ blog/ how-secure-mobile-app]
The cybersecurity diagram example "Mobile app security" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Neither company validated security certificates to make sure the app was sending the information to the right place. That left users vulnerable to “man in the middle attacks.” An attacker could trick the app into letting him access communications between the app and the online service. Neither the person using the app nor the online service would know the attacker was there." [consumer.ftc.gov/ blog/ how-secure-mobile-app]
The cybersecurity diagram example "Mobile app security" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
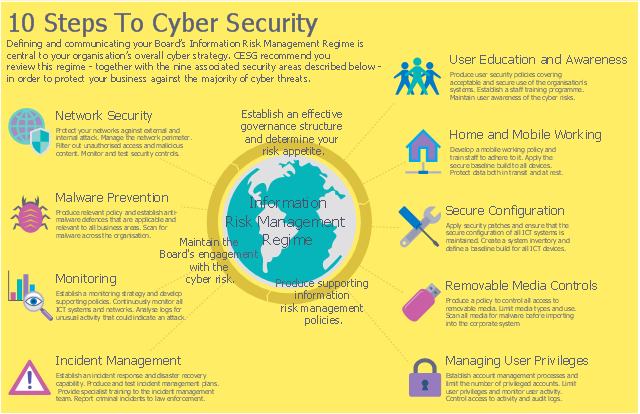
This example was designed on the base of the cybersecurity infographic from the website gov.uk. (Open Government Licence v3.0. nationalarchives.gov.uk/ doc/ open-government-licence/ version/ 3/ )
"10 Steps To Cyber Security...
Defining and communicating your Board’s Information Risk Management Regime (shown at the centre of the following diagram) is central to your organisation’s overall cyber strategy.
... the 9 steps that surround it are ...
- Secure configuration
- Network security
- Managing user privileges
- User education and awareness
- Incident management
- Malware prevention
- Monitoring
- Removable media controls
- Home and mobile working" [gov.uk/ government/ publications/ cyber-risk-management-a-board-level-responsibility/ 10-steps-summary]
The infographic example "10 Steps to Cyber Security" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"10 Steps To Cyber Security...
Defining and communicating your Board’s Information Risk Management Regime (shown at the centre of the following diagram) is central to your organisation’s overall cyber strategy.
... the 9 steps that surround it are ...
- Secure configuration
- Network security
- Managing user privileges
- User education and awareness
- Incident management
- Malware prevention
- Monitoring
- Removable media controls
- Home and mobile working" [gov.uk/ government/ publications/ cyber-risk-management-a-board-level-responsibility/ 10-steps-summary]
The infographic example "10 Steps to Cyber Security" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
Used Solutions
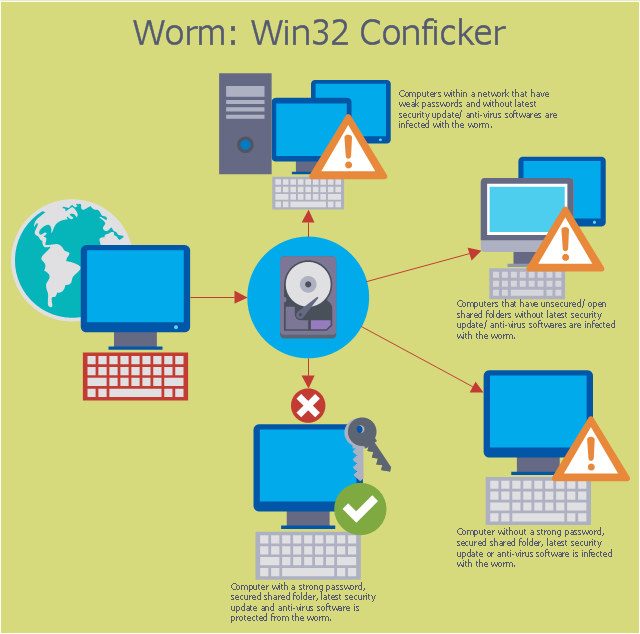
This computer security diagram example was designed on the base of the Wikimedia Commons file: Conficker.svg. [commons.wikimedia.org/ wiki/ File:Conficker.svg]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it. Unlike a computer virus, it does not need to attach itself to an existing program. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer." [Computer worm. Wikipedia]
The cybersecurity diagram example "Spread of Conficker worm" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"A computer worm is a standalone malware computer program that replicates itself in order to spread to other computers. Often, it uses a computer network to spread itself, relying on security failures on the target computer to access it. Unlike a computer virus, it does not need to attach itself to an existing program. Worms almost always cause at least some harm to the network, even if only by consuming bandwidth, whereas viruses almost always corrupt or modify files on a targeted computer." [Computer worm. Wikipedia]
The cybersecurity diagram example "Spread of Conficker worm" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
This example was designed on the base of the cybersecurity infographic from the website gov.uk. (Open Government Licence v3.0. nationalarchives.gov.uk/ doc/ open-government-licence/ version/ 3/ )
"10 Steps To Cyber Security...
Defining and communicating your Board’s Information Risk Management Regime (shown at the centre of the following diagram) is central to your organisation’s overall cyber strategy.
... the 9 steps that surround it are ...
- Secure configuration
- Network security
- Managing user privileges
- User education and awareness
- Incident management
- Malware prevention
- Monitoring
- Removable media controls
- Home and mobile working" [gov.uk/ government/ publications/ cyber-risk-management-a-board-level-responsibility/ 10-steps-summary]
The infographic example "10 Steps to Cyber Security" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"10 Steps To Cyber Security...
Defining and communicating your Board’s Information Risk Management Regime (shown at the centre of the following diagram) is central to your organisation’s overall cyber strategy.
... the 9 steps that surround it are ...
- Secure configuration
- Network security
- Managing user privileges
- User education and awareness
- Incident management
- Malware prevention
- Monitoring
- Removable media controls
- Home and mobile working" [gov.uk/ government/ publications/ cyber-risk-management-a-board-level-responsibility/ 10-steps-summary]
The infographic example "10 Steps to Cyber Security" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
Used Solutions
Cyber Security Degrees
For protection various cyber environments are developed and applied large variety of cyber security standards, techniques, security concepts and approaches with different cyber security degrees. The ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park offers the number of useful tools which will help network security engineers, cyber security specialists, network and computer analysts easily and visually depict the knowledge and skills for research and prevention of intrusions, about protection critical information and analysis of cyber incidents, and for how to assess threats and vulnerabilities.This computer security diagram example was designed on the base of the Wikimedia Commons file: Firewall.png.
[commons.wikimedia.org/ wiki/ File:Firewall.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed to not be secure or trusted. Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls are a software appliance running on general purpose hardware or hardware-based firewall computer appliances that filter traffic between two or more networks. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine. Firewall appliances may also offer other functionality to the internal network they protect such as acting as a DHCP or VPN server for that network." [Firewall (computing). Wikipedia]
The cybersecurity diagram example "Firewall between LAN and WAN" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
[commons.wikimedia.org/ wiki/ File:Firewall.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, a firewall is a network security system that monitors and controls the incoming and outgoing network traffic based on predetermined security rules. A firewall typically establishes a barrier between a trusted, secure internal network and another outside network, such as the Internet, that is assumed to not be secure or trusted. Firewalls are often categorized as either network firewalls or host-based firewalls. Network firewalls are a software appliance running on general purpose hardware or hardware-based firewall computer appliances that filter traffic between two or more networks. Host-based firewalls provide a layer of software on one host that controls network traffic in and out of that single machine. Firewall appliances may also offer other functionality to the internal network they protect such as acting as a DHCP or VPN server for that network." [Firewall (computing). Wikipedia]
The cybersecurity diagram example "Firewall between LAN and WAN" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
This example was designed on the base of the diagram from the article "How secure is that mobile app?" by N.V. Fleming on the website of the U.S. Federal Trade Commission (FTC).
"Neither company validated security certificates to make sure the app was sending the information to the right place. That left users vulnerable to “man in the middle attacks.” An attacker could trick the app into letting him access communications between the app and the online service. Neither the person using the app nor the online service would know the attacker was there." [consumer.ftc.gov/ blog/ how-secure-mobile-app]
The cybersecurity diagram example "Mobile app security" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Neither company validated security certificates to make sure the app was sending the information to the right place. That left users vulnerable to “man in the middle attacks.” An attacker could trick the app into letting him access communications between the app and the online service. Neither the person using the app nor the online service would know the attacker was there." [consumer.ftc.gov/ blog/ how-secure-mobile-app]
The cybersecurity diagram example "Mobile app security" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
Network Security Devices
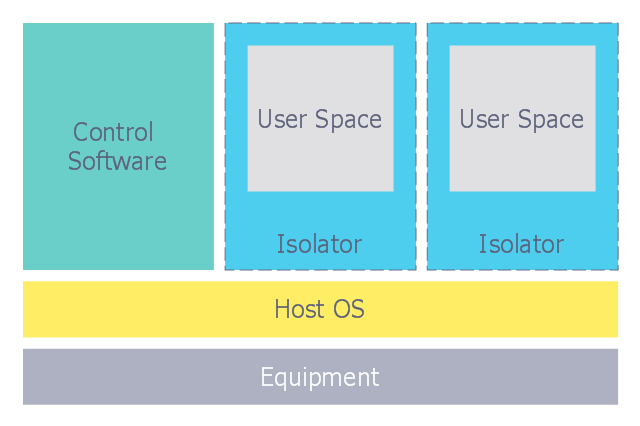
How to describe the necessity of using network security devices and visually illustrate this information? Now, it's very easy thanks to the ConceptDraw PRO diagramming and vector drawing software extended with Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park.This computer security diagram example was designed on the base of the Wikimedia Commons file: Diagramme ArchiIsolateur.png.
"Virtualization, architecture of an isolator."
[commons.wikimedia.org/ wiki/ File:Diagramme_ ArchiIsolateur.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, virtualization refers to the act of creating a virtual (rather than actual) version of something, including virtual computer hardware platforms, operating systems, storage devices, and computer network resources." [Virtualization. Wikipedia]
The cybersecurity diagram example "Isolator architecture" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
"Virtualization, architecture of an isolator."
[commons.wikimedia.org/ wiki/ File:Diagramme_ ArchiIsolateur.png]
This file is licensed under the Creative Commons Attribution-Share Alike 3.0 Unported license. [creativecommons.org/ licenses/ by-sa/ 3.0/ deed.en]
"In computing, virtualization refers to the act of creating a virtual (rather than actual) version of something, including virtual computer hardware platforms, operating systems, storage devices, and computer network resources." [Virtualization. Wikipedia]
The cybersecurity diagram example "Isolator architecture" was created using the ConceprDraw PRO software extended with the Network Security Diagrams solution from the Computer and Neworks area of ConceptDraw Solution Park.
IT Security Solutions
Dynamic of development computer and network technologies increases the need in modern cyber security strategies and IT security solutions to support security of your data, to ensure data privacy, and to protect your operations from the cyber threats. Thanks to the Network Security Diagrams Solution from the Computer and Networks Area of ConceptDraw Solution Park, the ConceptDraw PRO diagramming and vector drawing software is one of the unique IT security solutions for professional designing Network Security Diagrams.- Computer Security Threats
- | Cyber Security Degrees | | Computer Security Risk
- Conceptdraw.com: Mind Map Software, Drawing Tools | Project ...
- Network Security . Computer and Network Examples | Cisco security ...
- Diagramaticaly Pster Presentation Of Computer Security
- Make A Diagram Of Computer Security
- Design elements - Cybersecurity clipart | Cyber Security Degrees ...
- Cyber Security Degrees | 10 Steps to Cyber Security | Network ...
- Spread of Conficker worm | Network Security Diagrams | Spread Of ...
- Computer security diagram
- Computer security infographic
- Design elements - Cybersecurity connectors | Cyber Security ...
- Fork bomb | IT Security Solutions | Network Security Diagrams ...
- Isolator architecture | Network Security Diagrams | Network Security ...
- Design elements - Cybersecurity round icons | Cyber Security ...
- 10 Steps to Cyber Security | Network Security Diagrams | Network ...
- Design elements - Cybersecurity shapes | Cyber Security Degrees ...
- EFS Operation | Network Security Diagrams | Network Security ...
- Firewall between LAN and WAN | Network Security Diagrams ...
- ConceptDraw PRO Network Diagram Tool | Network Security ...